Over the past year, executive teams and board members across multiple industries have started to ask questions more forcefully about the risk posed by cybersecurity attacks. They are no longer content with technical reviews of their security controls and are asking questions related to the business impact of cybersecurity attacks. How much cyber risk do we have? Are we spending too much or not enough? How much can we reduce risk with the proposed info security budget? Should we buy cyber-insurance?

Goals of cyber value-at-risk models
Such questions have led to the development of value-at-risk (VaR) models, specifically designed for information security. Sometimes referred to as cyber VaR, these models provide a foundation for quantifying information risk and insert discipline into the quantification process. The goal of VaR models is two-fold:
- help risk and infosec professionals articulate cyber risk in financial terms, a language that everyone understands
- enable business executives to make cost-effective decisions and achieve a balance between protecting the organization and running the business
Organizations that have adopted VaR models for cybersecurity are able to drive the discussion about risk in more consistent, business-aligned terms. It also has allowed them to start making decisions based on financial data and to move progressively away from making decisions based on Fear, Uncertainty and Doubt (FUD).
Origin and definition of cyber VaR
In the financial services industry, value-at-risk modeling is a statistical methodology used to quantify the level of financial risk within a firm or investment portfolio over a specific time frame. Value at risk is measured in three variables:
- the amount of potential loss
- the probability of that amount of loss
- the time frame
Similarly, cyber VaR models use probabilities to estimate likely losses from cyber attacks during a given timeframe.
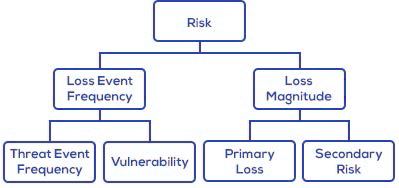
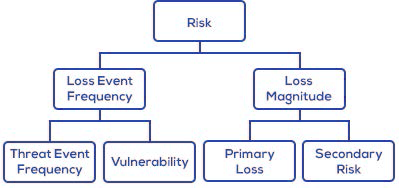 Many of the world's largest companies and organizations, such as the World Economic Forum, and standards bodies, such as The Open Group, are promoting the adoption of cyber VaR models. FAIR has emerged as the leading VaR model for cybersecurity and operational risk and as the only international standard.
Many of the world's largest companies and organizations, such as the World Economic Forum, and standards bodies, such as The Open Group, are promoting the adoption of cyber VaR models. FAIR has emerged as the leading VaR model for cybersecurity and operational risk and as the only international standard.
Perceived limits of cyber VaR
The adoption of cyber VaR models has been hampered by certain perceived limitations:
- Not enough data available
The biggest objection is that there isn't a sufficiently large set of historical data regarding the frequency and loss magnitude of risk events to complete quantifiable risk analyses.
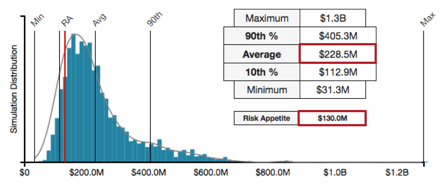 On the event frequency side, many organizations are experiencing that utilizing advanced estimation techniques along with mathematical simulations such as Monte Carlo allows them to estimate event frequency in the form of distribution of probabilities. The resulting shape of the distribution reflects the level of confidence in the data: flatter, if the level of confidence is low; spikier, around the most likely average value, if the level of confidence is high. In all cases, these organizations report that the result of the analysis is much better than just relying on guesstimates or "sticking a wet finger in the air".
On the event frequency side, many organizations are experiencing that utilizing advanced estimation techniques along with mathematical simulations such as Monte Carlo allows them to estimate event frequency in the form of distribution of probabilities. The resulting shape of the distribution reflects the level of confidence in the data: flatter, if the level of confidence is low; spikier, around the most likely average value, if the level of confidence is high. In all cases, these organizations report that the result of the analysis is much better than just relying on guesstimates or "sticking a wet finger in the air".
On the loss magnitude side, the challenge is related to the (understandable) resistance of organizations to freely share data that can be used to create industry-specific loss tables. Organizations using cyber VaR models rely on industry research and on the experience of vendors that market cyber VaR solutions such as RiskLens (disclaimer: the author is an executive of the company) to build loss tables that they can leverage for their risk analyses.
- Lack of standard risk definitions
Another challenge is related to the lack of standard definitions of risk within organizations. How risk is defined can vary from one person to another within the same organization. It is very common to see risk registers that should ideally list an organization's top risks. Often, the major problem is that many items in that list are not top risks, and some aren't risks at all. They should instead be classified as control deficiencies, vulnerabilities or threat communities.
A lot of the value from adopting risk models, such as FAIR, lies in providing a comprehensive and consistent definition of risk in the form of a common taxonomy or ontology. This enables everyone in the organization to use the same measuring stick and enable effective comparisons of risk scenarios.
- Support of limited number of scenarios
The first applications of cyber VaR models relied on conducting single analyses using elaborate spreadsheets. Comparing risk scenarios was a very complex and resource-intensive exercise and aggregating risk scenarios for enterprise-level assessments was a practical impossibility.
Recent, next-generation cyber VaR platforms, such as RiskLens, have removed those obstacles and designed enterprise-grade applications that can analyze a large number of risk scenarios simultaneously and in aggregate.
Information risk professionals are organizing
The recent pressure that corporate boards and executive management have placed on IT leadership for better reporting and management of cyber risk is prompting many organizations and risk professionals to create forums where they can learn about standard cyber VaR practices and can share use cases and real-life experiences.
The FAIR Institute was recently created as the forum where information risk and security professionals can learn more about the FAIR VaR standard and how to articulate and manage cyber risk from the business perspective. Consider joining the FAIR Institute and discover the benefits reserved for its members. Membership is free.