
Cyber insurance is an important element in the cyber risk management program, to enable the transfer of residual risks. As a result, insurance is often seen as the “doing nothing” option which represents a “moral hazard” to the insurer. This is far from the truth as policyholders must manage the non-insurable residual risks themselves in accordance with their risk appetite statements. Prudent policyholders partner with their brokers and underwriters to develop cost effective insurance coverage to minimize over-insurance and ensure they are not underinsured.
The current court cases covering disputes in high value cyber insurance claims demonstrate the importance of these considerations. A genuine risk appetite statement provides the foundation of this assessment process. It is written in a language which the cyber risk team can understand and be able to prioritize their mitigation program to fortify against the “residual risk” boundary.
Assessing the sufficiency of cyber insurance coverage is an important and difficult task. Sufficiency can be measured against the dimensions in coverage scope, insurable events, coverage limits and exclusions. The Open Group FAIR (Factor Analysis of Information Risk) cyber risk quantification framework is a useful tool to calculate the most cost effectiveness coverage.
The article explains how to apply the FAIR approach in the pre-loss risk assessment phase to guide the process in determining the sufficiency of the coverage by quantifying potential business losses.
 Denny Wan is the chair of the Sydney Chapter of the FAIR Institute and a cyber security expert with over 20 years experience in the Australian IT security sector. This article originally appeared on LinkedIn.
Denny Wan is the chair of the Sydney Chapter of the FAIR Institute and a cyber security expert with over 20 years experience in the Australian IT security sector. This article originally appeared on LinkedIn.
Insurance basics
Insurance, as a risk transfer mechanism as depicted in the following diagram:

Source: "Captives: An Efficient Tool for Catastrophic Losses," IRMI.com
As shown in the diagram, routine operational security risks (such as password management and anti-virus protection) are managed through the enterprise cyber risk management programs. The probability of loss is high but the loss value is not catastrophic. The ‘MUST RETAIN’ risk category of risk is not commercially attractive for insurance coverage due to the excessive premium relative to the insured value.
Other classes of cyber risks such as ransomware which are not routine but can result in significant financial loss are candidates for commercial insurance. The ‘CAN TRANSFER’ risk category can be covered by commercial insurance but the premium could become excessive if the coverage limit is set very high. The ‘tolerance level’ is adjusted to reflect the risk appetite of the organization through coverage limits and exclusions in the insurance policy. A common example is the excess (or deductible) which can be increased to lower premium. By accepting a higher claim excess, the policyholder has increased its risk appetite. Risks exceeding the tolerance level fall into the ‘SHOULD TRANSFER’ risk category. Policyholders might still decide to transfer the liability to the insurer by paying a higher excess.
Finally, extreme risk exceeding the ‘confidence level’ is managed under the approach of ‘self-insurance’. This level is set based on the risk appetite of the organization defined as the risk level it is willing to take in the pursuit of its strategy. This can be achieved by reserving capital to cover such loss events or designing the business strategy to minimize their exposure to such risk events. Defensive strategies such as withholding services or products in designated high-risk countries or jurisdictions.
To improve the profitability of commercial insurance, insurers target policyholders with a good risk profile through incentives such as no claim bonus, subsidized monitored home alarm systems and gym membership, for example under property and health insurances. Contrary to the perception of an adversarial relationship between policyholders and insurer leading to “moral hazard”, the right incentives structures can encourage them to become partners in managing their collective risk as discussed in the following papers:
Pro-active Cyber Insurance Pricing Model
Cyber Insurance Incentive Model
Key insurance terms
Insurance policies are binding legal contracts between the policyholders and insurers and must be reviewed by suitably qualified legal practitioners. This article does not provide any advice on insurance. This section explains some key insurance terms found in most policy documents:
Loss of Net Profit vs Gross Profit – Gross Profit is revenue less variable costs. Net Profit is Gross Profit less operating expenses for the period. It is common for the business interruption element of cyber insurance policies to provide cover for the loss of Net Profit as opposed to Industrial Specific Risks Insurance (ISR) or other commercial business policies which generally provide cover for the loss of Gross Profit.
An experienced and suitably qualified consultant should be engaged to quantify the revenue/profit at risk, provide advice on an adequate level of cover and the particular cyber policy wording.
Waiting period – This is a period of time after an event for which business interruption losses will not be covered. It is usually applied to every claim. This limits the amount claimable per incident. The policyholder must budget for this and manage their capital plan and cash flow accordingly to cope losses which may occur during the Waiting Period. Be sure to understand how the insurance policy calculated the time i.e. do they use business hours or normal hours.
Period of Indemnity – Also called “Indemnity Period”. Cyber policies will only provide cover for business interruption losses for a specified period of time, usually three months. Therefore, policyholders need to examine their BCPs and account for potential losses beyond the Indemnity Period. Policy wordings should be reviewed carefully to determine when the Period of Indemnity begins. The Ponemon 2017 Cost of a Data Breach Study shows US companies took an average of 206 days to detect a data breach. It is important for policyholders to understand the term “Indemnity Period” as defined in their policies. For instance, forensic examination of a data breach might conclude that the system intrusion is deemed to have occurred before the policy commenced but remained dormant until the intrusion was exploited resulting in the data breach, rendering it an “existing risk event” which might not be covered.
Moreover, there might be ‘extra expense’ such as sourcing from alternate suppliers at a higher cost. These expenses might not be covered by the insurance policy and should be budgeted for. Some policies have additional cover for ‘extra expense’ subjected to “economic test”. The economic test might state that the additional expenditure to mitigate the event should not exceed the amount that would potentially be lost during the indemnity period. Be sure to consult an experienced and suitably qualified consultant to get a full understanding of the coverage provided.
3rd Party Costs – Often the focus of cyber insurance is the cost to restore impacted systems. But the interconnected nature of IT infrastructure increases the likelihood of 3rd party claims. For example, under EU GDPR (General Data Protection Regulation) legislation, organizations who collect personal data are still liable even if the data is breached through their service providers. These data holders will make claim against their 3rd party service providers to offset their own liabilities. This is because their cyber insurance policy will not cover liabilities.
The FAIR quantification approach
The Open Group FAIR quantification framework can be used to evaluate the cost effectiveness of cyber risk mitigation solutions by estimating the potential loss attributed to insured loss events. The framework is depicted below:
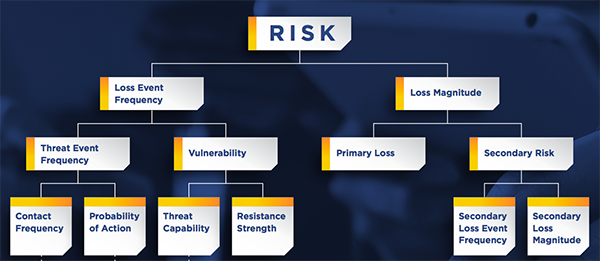
The analysis on the left side of the model breaks down the risk scenarios to its core components such as Threat Capability vs Resistance Strength. This approach helps to visualize alternate mitigation options such as “do nothing”, effectively shifting them into the “residual risk” bucket.
As discussed previously, residual risk can be managed through risk transfer mechanism such as insurance. Understanding the loss magnitude calculation is an important step in the assessment of sufficiency in insurance cover. The right side of the diagram above focus on the estimation of loss.
The FAIR taxonomy defines six forms of loss as depicted below:

Of the six forms of loss, Productivity, Response and Replacement are generally the forms of loss experienced as Primary Loss. Secondary Loss, occurs as a result of secondary stakeholders (e.g., customers, stockholders, regulators, etc.) reacting negatively to the primary event. Think of it as “fallout” from the primary event. An example would be customers taking their business elsewhere after their personal information had been compromised or due to the frustration experienced as a result of frequent service outages.
Two important considerations of Secondary Loss are that:
- It is always predicated on a primary event.
- It does not materialize from every primary event.
Another important aspect of Secondary Loss is that its effect on an organization can cascade. As losses pile up from initial Secondary Losses, additional secondary stakeholders may react negatively, compounding the effect until losses are so great that the organization fails completely (e.g., the demise of Andersen Consulting in 2002). This is the primary factor in deciding the boundary between commercial insurance and self-insurance. These considerations are often codified in organization risk appetite statements. But, unfortunately, the information is often not expressed in a format easily consumable to the management decision in the insurance coverage composition process. The FAIR quantification process is a key to enable a consensual approach to the interpretation of these risk appetite statements, to enable the prioritization process.
Related:
3 Tips on Evaluating Cyber Insurance with the FAIR Model
[Video] FAIRCON18 Panel: Optimizing Cyber Insurance Coverage
Planning the insurance claim process
To adequately transfer cyber risks to insurers, a business must first quantify their expected losses in the event of a cyber incident. This is normally done with reference to various scenarios.
Failure to adequately quantify their expected losses in the event of a claim could result in the business being under-insured, therefore retaining a portion of the risk they expected to transfer to insurers, or being over-insured and therefore paying unnecessarily high premiums.
A policyholder should ensure it has processes in place to estimate expected losses attributed to insured loss events. This process requires a good general understanding of their industry and their particular business environments, as well as a deep understanding of their policy wording and how it will be applied in the event of a claim.
This section explains the basic approach to the loss estimation process based on the six forms of losses in the FAIR framework.
Productivity loss – This is essentially losses due to business interruption.
Response cost – This is a commonly underestimated, confined to the cost to restore the IT systems and data. There could be significant additional costs to restore full business function after the IT systems and data have been successfully restored. For example, inventory and payment reconciliation and rescheduling of products and services delivery. These costs might not be covered by the cyber insurance policy.
Replacement costs – This includes the cost to replace physical assets which cannot be sufficiently restored or where there is little confidence that malware has been successfully removed.
Competitive Advantage Loss – Losses resulting from competitors taking market share from you by compromising intellectual property or other key competitive differentiators. The executive management team such as the chief financial officer might be the best source of estimation.
Fines, Judgements and Reputation Damage – Specialist law firms experienced in these areas of litigation could provide a good estimate based on precedent cases.
It is clear that these loss estimates require specialist skills which should be coordinated by an experienced and suitably qualified consultant to ensure transferable risks are identified and adequately quantified.
Conclusion
The traditional adversarial approach to insurance management is not a sustainable approach to manage cyber risks in the contemporary information-driven supply chain economy. The attack surface is expanding rapidly, and the loss can be catastrophic. Understanding the process, enabled by cyber risk quantification techniques, is an essential step to express enterprise risk appetite statements into cyber insurance cover. This will ensure sufficiency and sustainability for both the policyholders and insurers.
About the author:
Denny Wan is a cyber security expert with over 20 years experience in the Australian IT security sector. He is the chair of the Sydney Chapter of the FAIR Institute with deep expertise in Cyber Risk Economics. This is an effective approach for prioritizing cyber security investments and to explain its business values. He is a certified PCI QSA and CISSP. He is a postgraduate researcher at the Optus Macquarie University Cyber Security Hub researching cyber risk management in the supply chains. This is a useful model for managing 3rd party supplier risk under compliance framework such as APRA CPS 234.
About the reviewers:
Deven Raniga specializes in insurance claims and forensic accounting, with a particular focus on Business Interruption and Cyber insurance claims, as well as pre-loss quantification of Cyber and Business Interruption risks. He is a CPA, Chartered Loss Adjuster and an ANZIIF Senior Associate/Certified Insurance Professional, and has also completed the FAIR Analysis Fundamentals training course through RiskLens.
James Crowther is the General Manager of Agile Underwriting. He is an entrepreneurial risk and governance specialist, over 15 years experience in risk management, and commercial portfolio management gained at Lloyd’s of London. Specialisms include risk review and assessment, raising cyber resilience awareness and working with all key stakeholders to ensure enterprise cyber security risks are well understood and managed. Building on the Lloyd’s career, he progressed to lead multiple cyber insurance start ups in Australia and gained experience in pre risk identification, post risk and response services, data breach response framework development, which include cyber risk identification, impact assessments, crisis management, risk mitigation, public relations and business continuity planning. Acknowledged industry specialist on Cyber insurance, dealing with IT security incidents and data breaches effectively.
The 2019 FAIR Conference brings leaders in information and operational risk management together to explore best FAIR practices that produce greater value and alignment with business goals. Join us, September 24 & 25, 2019 at National Harbor, MD, near Washington, DC.









