Discipline Employees for Email Data Breaches? You May Also Discourage Them from Reporting
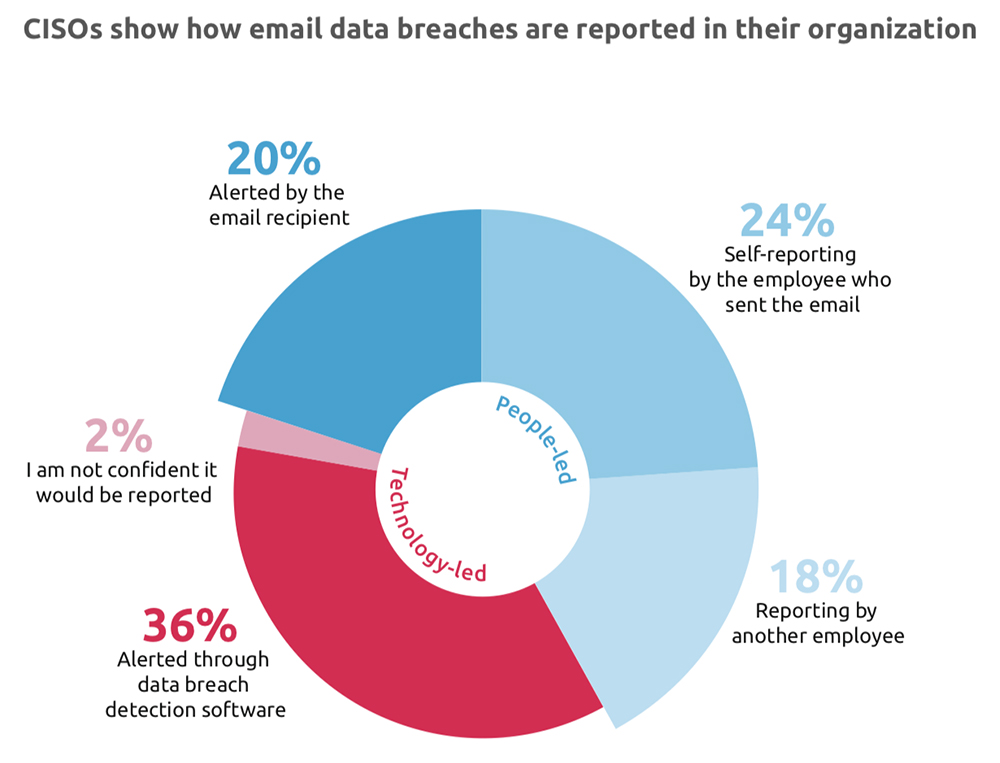
 A new study sponsored by email security solutions vendor Egress found that CISOs surveyed rely more on employees reporting email data breaches than data breach protection software to alert them to the loss event. In fact, 24% relied on the responsible employee to self-report the breach.
A new study sponsored by email security solutions vendor Egress found that CISOs surveyed rely more on employees reporting email data breaches than data breach protection software to alert them to the loss event. In fact, 24% relied on the responsible employee to self-report the breach.
At the same time, the CISOs said that their organizations were likely to reprimand or fire the responsible employee.
- “In nearly 50% of incidents the individual responsible for the breach received a formal warning or was disciplined.
- “On 27% of occasions, the employee was fired. Financial services organizations appear to take personal responsibility most seriously, terminating an employee’s contract in 31% of cases.”
The Egress report concludes that “blame culture deeply impacts data breach reporting. It makes sense: if you think you’re going to be reprimanded for something, you’re less likely to come forward about your or others’ mistakes.
“Considering that ‘an employee being tired/rushed/stressed’ was identified as the biggest single cause of severe data breach incidents, it is reckless to assume these same individuals will self-report – or, if they’re particularly busy, even realize they’ve caused a breach.”
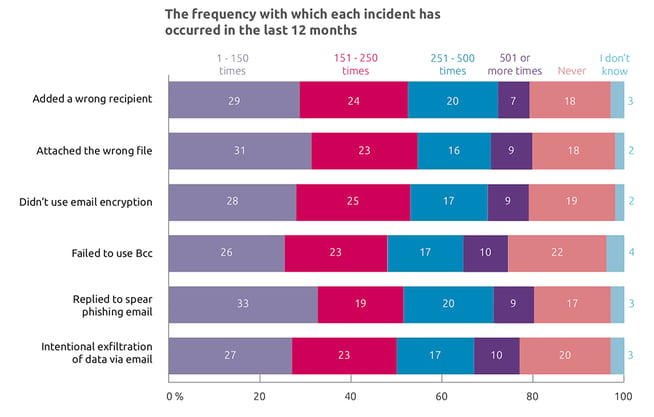
Indeed, the types of incidents covered by the survey show that mostly data breach by email is the result of dumb mistakes or poor training (including falling for phishing messages) not malicious intent. Human nature being what it is, the outlook for improvement isn’t bright.
Vendors like Egress, of course, suggest that you get around human nature with machine learning, encryption and other software solutions. But how do you get a handle on your particular email-mediated – or human-mediated – risk, let alone the cost vs. benefit of a solution?
As Chad Weinman of RiskLens wrote in a ThreatPost article, Assessing the Human Element in Cyber Risk Analysis, “most cybersecurity professionals don’t know where to start.
“Often organizations are shortsighted and look at only the immediate phishing or misdirected emails rather than what the impacts are further down the attack chain. This can lead to over-stating or under-stating the actual risk.”
FAIR analysis shows the way, as Chad wrote, in two steps:
“First, is asking what’s the likelihood that the employee will fall for a phishing email or accidentally forward a spreadsheet with customer sensitive information again? Second, what is the probability this action materializes into a data breach or system disruption — and what is the potential cost of these loss events?”
For a more detailed look at the process, read this blog post: Anatomy of a FAIR Risk Analysis: Confidential Data in Email.
“The bottom line is, there is a way to assess the human element,” Chad wrote. “Focus on defining and costing out the ultimate events that can cause your organization loss, not the people who set the chain in motion.”









