FAIR-MAM One Year Out: What Have We Learned about Material Cyber Risk?
It’s been a year since we debuted the FAIR Materiality Assessment Model at the 2023 FAIR Conference, an event covered by The Wall Street Journal, calling FAIR-MAM “a model to estimate damages from a cyberattack—a calculation that companies struggle to make as hacks play out over days and weeks.” (Read the article: New Calculator Aims to Measure Companies’ Cyberattack Damages)
As you’ll recall, at that time there was plenty of materiality anxiety in the air. The Securities and Exchange Commission was about to bring into effect its new rules for cyber risk incident disclosure, mandating that events resulting in material impact on the bottom line must be disclosed by regulated companies within four days of determining “materiality” – but that term was left to the companies to know it when they see it.
We hosted a well-attended session at FAIRCON23 on SEC cyber risk disclosure with star witness David Hirsch, then the cyber rules enforcement chief for the SEC.
Hirsch, now in private practice, returns for a FAIRCON24 panel discussion:
CISO Liability: How Not to Get Singled Out in an Evolving Regulatory Environment
Tuesday, October 1 at 1:30 PM
Also featuring
- Nick Sanna, Founder, FAIR Institute (Moderator)
- Mark Tomallo, CISO, Victoria's Secret
- John Winter, Chief Legal Officer and Counsel, Liberty Latin America
Read this interview with David Hirsch for his latest thinking. He maintains that by and large the SEC succeeded in its goal to elicit more public reporting without provoking, as he says, “a rush to disclosure” to meet a four-day deadline.
What Have We Learned about Material Impact of Cyber Risk since the Introduction of FAIR-MAM?
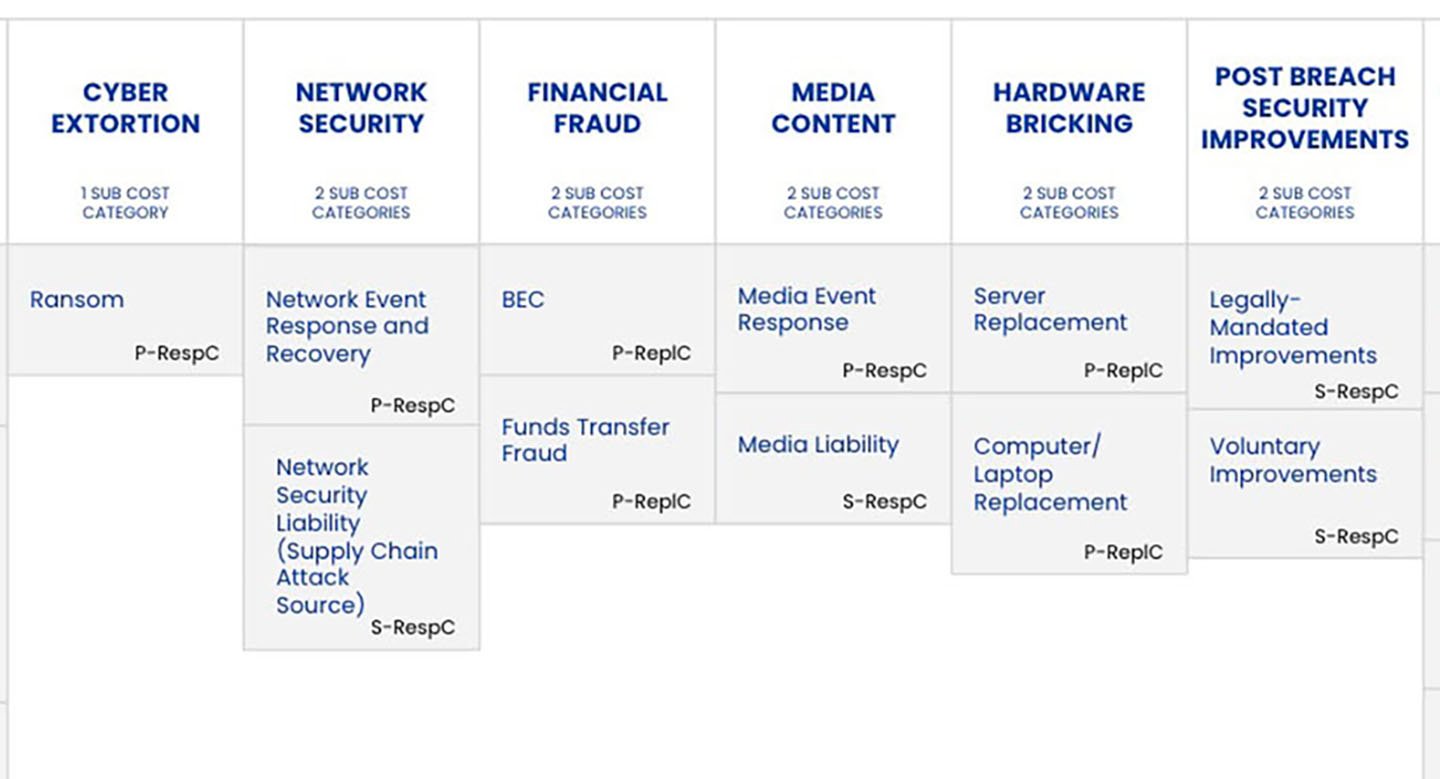
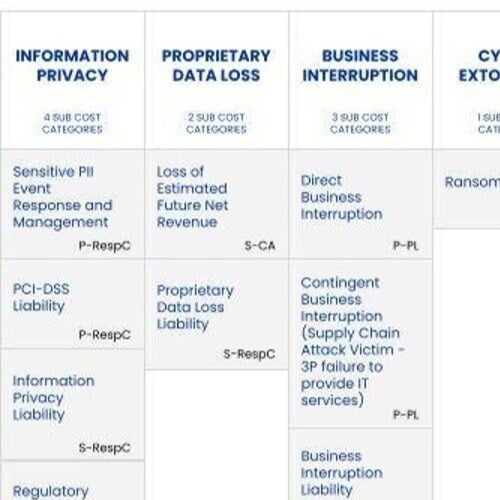
Beyond the narrow issue of reporting to the SEC or other regulators, the FAIR Materiality Assessment Model is an open financial loss model customizable to any organization’s cost structure to help report financial risk internally and inform cybersecurity investment and management decisions for a full range of custom cyber risk scenarios.
FAIR-MAM is also the driver behind the FAIR Institute’s informational website How Material Is that Hack? that analyzes breaches, including those disclosed in an SEC Form 8-K, and estimates their ultimate losses. Safe Security, the Institute’s Technical Advisory provides the analysis and modeling capabilities.
 For a look at what’s been learned from the past year from the use of FAIR-MAM and by watching the 8-K action, we turned to Erica Eager, the creator of FAIR-MAM, for a brief Q&A.
For a look at what’s been learned from the past year from the use of FAIR-MAM and by watching the 8-K action, we turned to Erica Eager, the creator of FAIR-MAM, for a brief Q&A.
Q: What’s the latest count of breaches estimated with FAIR-MAM for the Hack website?
A: Altogether we have modeled 15 supply chain attacks and 22 single party hacks. Some of the recent ones are:
- CDK (supply chain source - major player among auto sales, a supplier to ~50% of the new car dealers and ~4% of used car dealers)
- AutoNation (victim of the CDK hack)
- Delta Air Lines (victim of CrowdStrike supply chain system outage)
- Snowflake (supply chain source although Snowflake’s network was never accessed by the attacker – attacker used stolen login credentials to gain access to customer databases hosted on Snowflake infrastructure where MFA was not employed)
- Ticketmaster (victim on Snowflake’s infrastructure)
Q: What’s been the response to the SEC’s new disclosure rules?
A: For the most part, companies have been very good about reporting an incident on a Form 8-K. In fact, the SEC noted in a statement in May that many 8-Ks are being filed despite no estimation of materiality. The SEC encourages companies to continue to be forthcoming but to word their 8-Ks in such a way as to not confuse investors. Generally, public companies are filing 8-Ks after a breach whether they think the hack will be material or not.
Q: Any patterns you see in the data suggesting trends?
A: Supply chain attacks/outages are becoming much more prevalent, with significant industry-wide or economy-wide impact (Change Healthcare, Snowflake [no attack on Snowflake's network but Snowflake did not insist on MFA for its B2B customers] CDK, CrowdStrike, etc.)
As is to be expected, smaller companies with very large breaches of sensitive personal data are at risk of experiencing a company-killer data breach if they have to assume all of the response costs to the data record holders (National Public Data, Slim CD, etc).
Q: How have we improved and expanded the 'How Material Is that Hack' site?
A: We have split attacks between Supply Chain and Single Party attacks. We also include certain attacks if they are particularly interesting, even if they are not a public company. For example we just added Slim CD (a PCI payment processor that is a minor competitor of Square) and National Public Data (the company that exposed 272M Social Security numbers) because there are small companies with poor security who have processed some of the most sensitive personal data.
Q: What have we learned in the past year about materiality in cyber risk analysis?
A: Some of the most important considerations in determining materiality for a company are:
- For a ransomware attack with Business Interruption, it is important to determine how much of a company's revenue is what we refer to as "delayed" (for example, the company's revenue collection capability may be interrupted but the revenue is still owed to the company during the interruption regardless of when it is collected).
- Huge data breaches of very sensitive data can be caused by very small companies with <$5M in revenue.
- Many of the largest supply chain incidents do not necessarily translate into an immediate loss for the source company.
Q: Has the FAIR-MAM model been flexible enough to assess loss magnitude for any type of risk scenario?
A: Safe Security has just added AI Risk to its portfolio of risk scenarios and FAIR-MAM has proven its flexible and modular nature. There was no need to add to the original 10 modules or the first level loss categories of the FAIR-MAM framework.
Join us at the 2024 FAIR Conference to learn more about FAIR-MAM and its advanced methodology for estimating the financial impact of data breaches and other cyber loss events. Register for FAIRCON24 now!









