Every profession has its own language/vocabulary, whether it is the medical profession, law, or information technology. The medical and law professions have been around for hundreds of years and have established their professional vocabulary, however, IT, only around a few decades, has not developed a very mature vocabulary.
There are several words used in our profession that can be interpreted to have similar meanings. In FAIR™ (Factor Analysis of Information Risk) practice, they really mean different things. Take Risk, Threat, and Vulnerability; to the general public they basically mean the same thing. Even to many IT professionals, they are interchangeable. For an IT security professional, Threat and Vulnerability are components of the definition of Risk.
However, in FAIR practice, these words have an even deeper meaning. FAIR practitioners go a step further and put measurements around these words so they can be more definitive and separate in their meaning and value. Allowing these words to be interchangeable can confuse our IT colleagues and the leaders in our organizations.
 Paul Frenken, Enterprise Architect, World Wide Technology, is a senior technology executive with 25+ years of experience designing and implementing architectural roadmaps that maximize revenue and optimize processes.
Paul Frenken, Enterprise Architect, World Wide Technology, is a senior technology executive with 25+ years of experience designing and implementing architectural roadmaps that maximize revenue and optimize processes.
Risk
Let’s first look at Risk. According to the dictionary, Risk is the possibility of something bad happening. It involves uncertainty about the effects or implications of activity with respect to something that humans value, often focusing on negative, undesirable consequences. It’s the “unknown”, “what if”, the “ambiguous”.
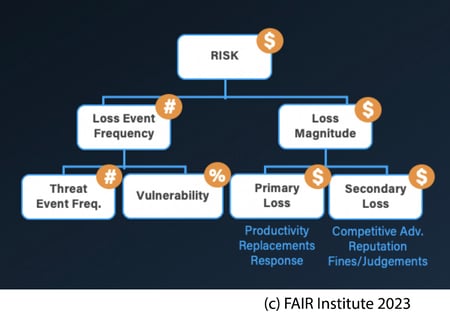
FAIR defines Risk quantitatively by placing a couple of parameters into the definition such as how often the losses are likely to happen (Loss Event Frequency), and how much the loss is likely to cost (Loss Magnitude). These parameters help the FAIR practitioner quantify the risk.
FAIR definition: “Risk is the probable frequency and probable magnitude of future loss.”
An example would be: “Ransomware in our network could impact our systems between 3 and 9 times a year and cost us between $10k – 250k.” It does not say that ransomware is present, it states a range of probable outcomes if present, based on the organization’s experience and industry historic data.
 Read more blog posts by FAIR Institute members
Read more blog posts by FAIR Institute members
We encourage content contributions from the FAIR community
Threat
Threat is commonly defined as an expression of intention to inflict harm, injury, or damage. An example is having an intent of using ransomware to inflict harm or damage to an organization. In the FAIR book Measuring and Managing Information Risk, threats are usually described as actors, communities, or natural disasters. It is easiest to think of threats linked to a group or natural disaster, such as Russian and Chinese-backed crime syndicates or flood, earthquake, and tornado; these intentions or events typically require the negative intent of action against an organization to be considered; but a non-malicious insider mistakenly causing a data breach could also be a threat actor.
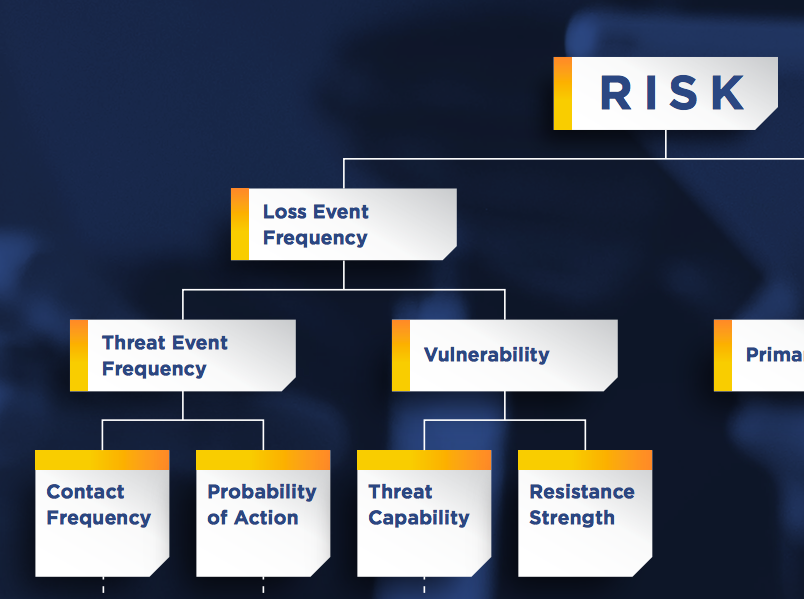
In essence, a Threat must have the potential to inflict loss. As part of quantifying Loss Event Frequency, a FAIR analyst quantifies Threat Event Frequency, the probable frequency within a given time frame that threat agents will act in a manner that may result in a loss.
Vulnerability
Vulnerability is commonly defined as the capability of being physically or emotionally wounded. In FAIR, vulnerability is a condition that increases the capability of being harmed. For example, being currently behind in OS patching that can allow ransomware to exploit and infect machines. Because we are behind in our patching schedule, there may be a probability of future harm but that does not mean it will happen.
In FAIR, Vulnerability is expressed as a percentage representing the probability that a threat agent’s actions will result in a loss; with Threat Event Frequency, it is a key factor in determining Loss Event Frequency.
The layperson and our IT teammates will often interchange these words as they describe a danger to the organization. When used properly, these words reflect completely different definitions and descriptions. It is up to the FAIR practitioner to continue to educate their fellow IT professionals and business colleagues in the proper use of these words. As FAIR practitioners, we must use the words correctly when we describe a risk (or probable loss exposure) and resist the practice of interchanging terminology. When appropriate, gently correct our fellow colleagues about how to use these words to describe dangerous situations.
Like other professions, it will take time to institute a universal vocabulary but as FAIR professionals, it is up to us to set and publicize the standard of the proper use of the terms Risk, Threat, and Vulnerability.
Read this next:
What Is Cyber Risk Quantification (CRQ) and How Does It Help Risk Management Decisions? by Jack Jones