
 The FAIR Institute’s “How Material Is That Hack?” website leverages the FAIR standard for estimating loss magnitude from a cybersecurity incident and is aligned to the SEC requirements for reporting Materiality on Form 8-K. As such, all financial output for a hack follows a strict taxonomy of loss categories and definitions of terms used. This blog is an ongoing source of clarification of this taxonomy and its definitions.
The FAIR Institute’s “How Material Is That Hack?” website leverages the FAIR standard for estimating loss magnitude from a cybersecurity incident and is aligned to the SEC requirements for reporting Materiality on Form 8-K. As such, all financial output for a hack follows a strict taxonomy of loss categories and definitions of terms used. This blog is an ongoing source of clarification of this taxonomy and its definitions.
Erica Eager is Sr. Director - CRQ at Safe Security, Technical Advisor to the FAIR Institute
Primary vs. Secondary Loss
According to FAIR, all losses are classified as either Primary or Secondary.
Primary Loss
Primary losses materialize for primary stakeholders directly as a result of a cyber incident. In order for a loss to be considered primary, it has to be unrelated to secondary stakeholder reactions. Examples of primary loss include:
- Lost gross profit margin from operational outages
- Incremental operating costs from workarounds due to operational outages
- Response costs associated with the restoration of functionality performed by third party service providers
- Record holder response costs such as breached record discovery cost and breach notification or call centers
Secondary Loss
Secondary losses are dependent on decisions made by third parties in connection with a cyber incident.The primary stakeholder is not in control of those decisions. Examples of secondary losses include:
- Financial penalties and/or mandatory cybersecurity improvement orders imposed by regulatory authorities
- Legal settlements related to the cyber incident, whether they are class action suits or not
- Reputational damage such as:
>>Loss of future net revenue to the company from a reduced customer retention rate post-breach or a competitive disadvantage due to the theft of IP & trade secrets
>>A higher cost of future capital due to a reduced credit rating
>>Higher cybersecurity premiums and/or reduced coverage
Quantitative vs. Qualitative
The SEC regulations state that both Quantitative and Qualitative Materiality factors must be considered when assessing the material impact of a cyber incident.
One should note, however, that if Qualitative factors materialize, they then become Quantitative factors. For example, sensitive personal data is exfiltrated as part of a cyber incident. Therefore, the possibility of a lawsuit settlement is accounted for as a risked Qualitative loss factor. Soon after the incident, a class action lawsuit related to the breach of sensitive personal data is filed. The risked loss – Qualitative loss factor – of a lawsuit settlement increased since the likelihood of experiencing this loss increased. Eventually, the parties agree to settle. Again, the lawsuit settlement Qualitative loss factor increases. As losses related to that settlement are finalized, they become Quantitative loss factors.
Quantitative
Quantitative factors are Primary Losses and have been referenced by the SEC in the past as follows, “Quantitative materiality assessments often are made by comparing adjustments to revenues, gross profit, pretax and net income, total assets, stockholders' equity, or individual line items in the financial statements.”
Qualitative
Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure, the SEC's recent ruling, stated, “The rule’s inclusion of “financial condition and results of operations” is not exclusive; companies should consider qualitative factors alongside quantitative factors in assessing the material impact of an incident.”
The SEC further defined Qualitative factors as follows:
“By way of illustration, harm to a company’s reputation, customer or vendor relationships, or competitiveness may be examples of a material impact on the company. Similarly, the possibility of litigation or regulatory investigations or actions...”
Materiality
The SEC stated in its recent ruling that the following factors must be considered when weighing the potential materiality of cyber incidents:
- The importance of any compromised information
- The impact of the incident on the company’s operations
- The nature, extent and potential magnitude of incidents as they relate to any compromised information or the business and scope of operations
- The range of harm that such incidents could cause including harm to a company’s:
>>Reputation
>>Financial performance
>>Customer and vendor relationships - The possibility of litigation or regulatory investigations or actions including regulatory actions by state and federal governmental authorities and non-US authorities
The SEC has always refused to rigidly define Materiality. Its approach to considering what is material, “...is consistent with the standard of materiality articulated by the U.S. Supreme Court in TSC Industries v. Northway, 426 U.S. 438, 449 (1976) (a fact is material “if there is a substantial likelihood that a reasonable shareholder would consider it important” in making an investment decision or if it “would have been viewed by the reasonable investor as having significantly altered the ‘total mix’ of information made available” to the shareholder).”
In its SEC Staff Accounting Bulletin: No. 99 - Materiality, the SEC addressed the potential fallacy of using the materiality ‘rule of thumb’ 5% number adopted by many registrants. While the bulletin was specifically addressing materiality of misstatements, the same principle applies to materiality when assessing the impact of cyber incidents. Specifically, the SEC stated in the bulletin, “Evaluation of materiality requires a registrant and its auditor to consider all the relevant circumstances, and the staff believes that there are numerous circumstances in which misstatements [including undisclosed estimates relating to future potential materiality] below 5% could well be material.”
Each company determines its own materiality threshold for reporting a cyber incident to the SEC on Form 8-K.. FAIR MAM is a tool that enables a company to calculate defensible loss magnitude for both Quantitative and Qualitative factors in real time as forensic investigators, legal advisors and operations teams provide continual updates related to the ‘nature, extent and potential magnitude of incidents as they relate to compromised information or the business and scope of operations.’
Example report from How Material Is That Hack
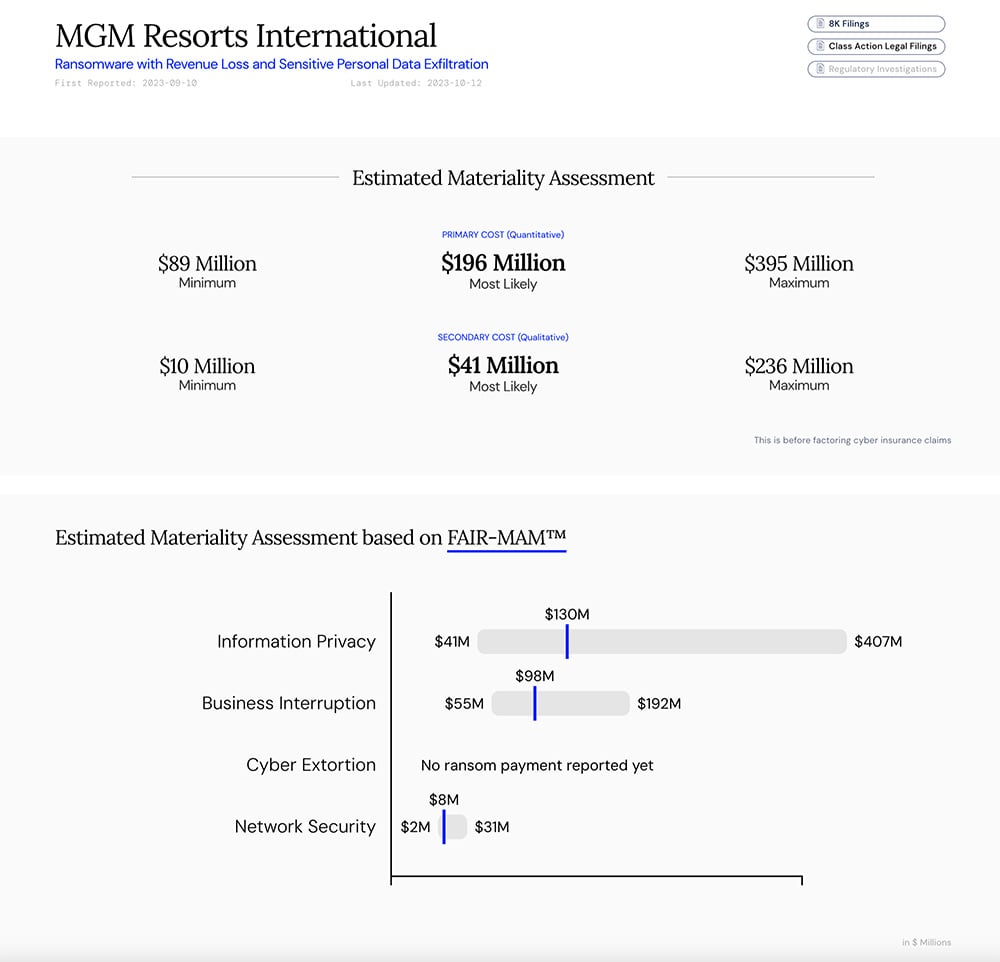
Visit the “How Material Is That Hack?” website.









