 Although I may be considered part of the “old guard” among FAIR analysts, I would by NO means call myself an expert in quantitative risk analysis using FAIR. I’m a very firm believer in the mindset of “getting better every day.”
Although I may be considered part of the “old guard” among FAIR analysts, I would by NO means call myself an expert in quantitative risk analysis using FAIR. I’m a very firm believer in the mindset of “getting better every day.”So I'm constantly thinking about the skills and areas of focus that will not only help me, but also my clients get better at our chosen profession, quantitative cyber risk analysis. Over the years, that focus has spanned from the importance of scoping an analysis, identifying what to shoot for when gathering data, and breaking down things to consider when presenting results.
As I’ve gained experience, and shifted roles, not only conducting analysis, but also helping organizations design and develop quantitative cyber risk programs, the skillsets I’ve needed to refine have changed as well. With this new perspective, I wanted to share two areas of focus that I’ve tried to get better at every day.
Understanding the Purpose
It’s been my experience that most risk analysts like the idea of seeing their risks in dollars and cents. They understand that it could gain them tremendous credibility among their constituents in their other lines of business, as well as provide a level of clarity for decision making that their previous approach just could not provide.
With these outcomes in mind, I’ve seen most new organizations work themselves into a frenzy to start analyzing quantitatively as quickly as possible before they ever ask themselves, what I consider to be the most important question of all, “What is the purpose of our analysis work?” Another way to look at this would be, “What are we trying to achieve”, or “What is the question we need to answer?”
Examples of compelling reasons to analyze risk quantitatively might include: the inability to confidently identify top risks; the inability to measure and clearly communicate the cost/benefit proposition of cyber risk management efforts; difficulty communicating about risk with executive stakeholders; unproductive religious debates about whether something represents high/medium/low risk.
From an analysis perspective, having this information is directly correlated to my success or failure in my efforts going forward. How would I know if I delivered on management's ask if I didn’t know what it was in the first place? Having this information also helps to inform:
- How complex or simple an analysis can be
- How precise estimates need to be
- What existing data we can leverage vs new data points required
- A rough estimate of the level of effort needed to complete the analysis
Understanding How the Loss Takes Place
As an analyst at heart, something I’ve tried progressively to get better at is gaining a greater understanding of the steps that lead to the loss. Some organizations would call this an attack chain – ultimately for me, I’d just like to know how the event starts and ends in loss.
From an analysis perspective, this helps to surface:
- What assumptions we’re working from and what the group does and does not know.
- Who else do we need to involve in our analysis. What SMEs, or external data points do we need to reference?
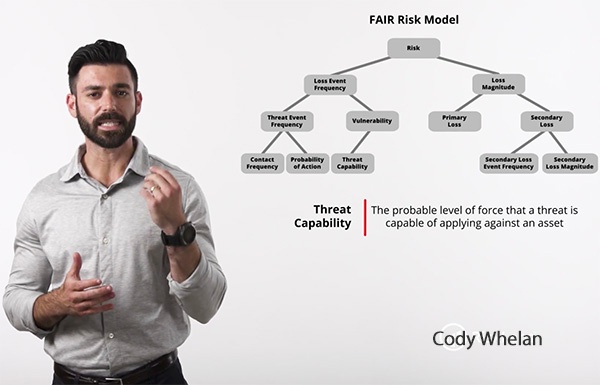
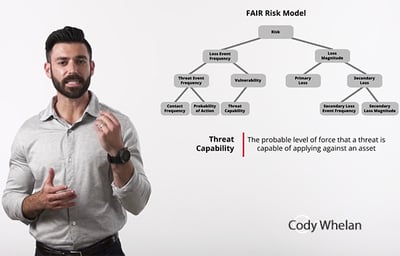
- How do we map this analysis to FAIR? Not only what represents Contact Frequency and Threat Event Frequency, but where do we have the most reliable data points?
I’ve found that having a clearer picture of this will reduce rework, follow ups and overall level of stress.
Get a complete education in cyber risk quantification from Cody Whelan and other experienced instructors in the FAIR online training course from RiskLens Academy. Read more by Cody.









