Threat Intel Meet Risk. Risk Meet Threat Intel. FAIR Makes the Match

As Wade Baker, Co-founder of Cyentia Institute, said, “blending threat intel and risk management should be a no-brainer” for the good of the organization. But different teams, different mentalities can create a gap. Risk management tends to be high level and strategic, Wade said, and threat intelligence very much in the weeds and tactical.
A panel discussion at the 2024 FAIR Conference turned into a brainstorming session on how to combine the MITRE ATT&CK framework for threat intelligence and the FAIR standard for quantitative cyber risk analysis to create a common language and mindset.
In the discussion with Wade (at right in the photo) were Vidit Baxi (left), Co-Founder & CISO, Safe Security, and Jon Baker (center), Director & Co-Founder, Center for Threat-Informed Defense, MITRE Engenuity.
Watch the video: ATT&CKing Cyber Risk Quantification
Key Tips from the Discussion on How to Combine FAIR and MITRE ATT&CK to Accelerate Cyber Risk Analysis and Threat Intelligence
1. Cyentia Institute’s IRIS Report is a good starting point to get a sense of where your organization stands on the two classic factors of FAIR, frequency and magnitude of loss events. This latest edition of IRIS covers ransomware with breakouts by industry. You can use IRIS to spot the most likely ransomware attack vectors coming at your organization.’
2. What to do with that knowledge? MITRE ATT&CK is a huge knowledge base of known tactics and techniques (TTPs) of attackers as well as the mitigations for each TTP – an opening for risk managers, Jon said, “to talk to your Cyber Operations team” about implementing those mitigations.
Jon presented two resources from his organization for next steps.
>>A Technique Inference Engine helps you predict the likely moves of an attacker after landing on your system; useful for building risk scenarios of benefit to both risk and threat teams. >>A Mappings Explorer maps TTPs to controls and vice versa, empowering, for instance, a risk analyst to ask the compliance team about implementation of a specific control to gain understanding of the extent to which a TTP is being mitigated.

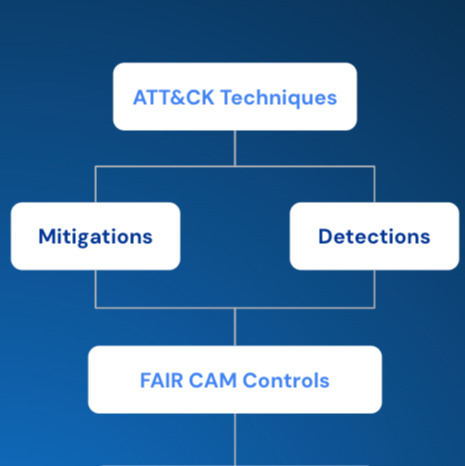
3. Vidit discussed the many benefits to cyber risk analysis with FAIR by combining MITRE ATT&CK and FAIR-CAM (the FAIR Controls Analytics model that measures the effectiveness of cybersecurity controls) – particularly to develop solid data to quantify the factors on the Loss Event Frequency side of the model (see the chart above).
Vidit took the discussion deeper with examples of meeting TTP’s with control functions as identified by FAIR-CAM, as in this example. (Note: the FAIR Institute’s FAIR-CAM Controls Library describes how each control operates and its value in a cyber risk management program.)
The result for risk management and threat intel teams is a “common language and a way in which we can have conversations and exchange data in a way that makes sense to both the teams,” Vidit said.
The factors include:
>>Threat Event Frequency, profiling threat actors, mapping to their relevant TTPs and your relevant controls for a refined view of TEF
>>Susceptibility (to attack), a factor determined by two subfactors:
>>Threat Capability, based on 152 profiles of threat actor groups in ATT&CK, clarifying their skill sets and tools
>>Resistance Strength - gauging current risk posture (by vulnerabilities, misconfigurations, etc.) mapped to controls and TTPs.

Vidit took the discussion deeper with examples of meeting TTP’s with control functions as identified by FAIR-CAM, as in this example. (Note: the FAIR Institute’s FAIR-CAM Controls Library describes how each control operates and its value in a cyber risk management program.)
The result for risk management and threat intel teams is a “common language and a way in which we can have conversations and exchange data in a way that makes sense to both the teams,” Vidit said.
Watch the video of the FAIRCON24 panel discussion: ATT&CKing Cyber Risk Quantification









