
 The MIT Technology Review recently published an article about what they called “cyber threats.” While the article identifies trending attack methods and scenarios to be concerned about, none of the things that made the list are actually threats.
The MIT Technology Review recently published an article about what they called “cyber threats.” While the article identifies trending attack methods and scenarios to be concerned about, none of the things that made the list are actually threats.
Keep in mind that a threat is a person, group of people, force of nature, etc. that can act against an asset in a way that results in loss and take a look at the list MIT published:
- “More huge data breaches”
Data breaches may be the outcome when threat actors act against your assets and overcome your defenses, but breaches are not the threat actors themselves. The breach is not the person or thing taking the action, it is the result of the action. - “Ransomware in the cloud”
This is a method that threat actors may employ, but ransomware itself is not a threat. - “The weaponization of AI”
Until AI takes over and independently decides to pursue threat actions against organizations, AI will not be a threat. Like ransomware, it will continue to be a tool threats use in their efforts to cause loss. - “Cyber-physical attacks”
While certainly concerning, cyber attacks against physical infrastructure are another type of attack threat actors may pursue. - “Mining cryptocurrencies”
Threat actors may harness your computer’s processing power to mine cryptocurrencies, but the mining itself isn’t a threat.
What the MIT Technology Review presented is a confusing list of outcomes and attack methods all grouped under the misused term “threats.”
Articles like this reinforce the need for risk management professionals, cyber security analysts and managers, and the cybersecurity press to align on common vocabulary in order to improve communication and enhance our collective effectiveness and credibility.
Toward that end, let’s revisit the definitions of the threat-related terms used in the FAIR model and FAIR-based analysis.
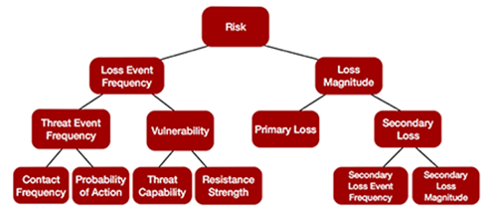 How do you identify a threat? Ask yourself “who or what is capable of acting against my asset in a way that could cause loss?” A threat can be a specific person, a group of people like hacktivists or cybercriminals, a force of nature like a tornado, or a self-propagating virus (whether of the type that infects computers or humans.) Whether sentient or not, all of these entities act on assets in a way that can result in loss. That’s what makes them threats. None of the items on MIT’s list act against assets; they are ways to act against assets or they are outcomes when cybercriminals successfully act against assets.
How do you identify a threat? Ask yourself “who or what is capable of acting against my asset in a way that could cause loss?” A threat can be a specific person, a group of people like hacktivists or cybercriminals, a force of nature like a tornado, or a self-propagating virus (whether of the type that infects computers or humans.) Whether sentient or not, all of these entities act on assets in a way that can result in loss. That’s what makes them threats. None of the items on MIT’s list act against assets; they are ways to act against assets or they are outcomes when cybercriminals successfully act against assets.
Threat event frequency refers to the number of times over a given timeframe (typically a year) that a threat will act against the asset you’re concerned about in a way that could result in loss. How many times will a hurricane threaten a processing facility, possibly taking it offline? How many times will nation-state hackers attempt to breach the confidentiality of your organization’s sensitive information? Note that the threat event is the attempt — once the threat has impacted the asset in a way that causes realized losses, a loss event has occurred.
Whether a loss event occurs depends on the asset’s vulnerability to the given threat event. Vulnerability, in FAIR terms, is the percentage of threat events of the type that are in-scope for your analysis that will result in loss.
Vulnerability is derived from threat capability and resistance strength. How skilled, well-resourced and knowledgeable are the attackers? How much skill, knowledge, and resourcing is required to overcome the controls defending the asset from threat events? These two variables are measured using percentiles along the threat capability continuum, a spectrum ranging from the most inept attackers to the most advanced. While analysts rarely need to estimate at this level of the model, it’s critical that you understand what Threat Capability and RS represent and how they work so you’re thinking with the right mindset when you estimate Vulnerability directly.
If we are all diligent in our use of these threat-related terms we can contribute to the eventual adoption of the FAIR lexicon, a critical step in the advancement of the risk management profession toward better communication and clearer thinking.
To learn more about the variables and vocabulary of the FAIR model, enroll in FAIR Analysis Fundamentals training today.
Related:
Loss Event Frequency Explained in 3 Minutes [Video]
Vulnerability in Risk Analysis Explained in 2 Minutes [Video]









