FDA Proposes a “Probabilistic,” Scenario-based Approach for Medical Device Cyber Risk

 The U.S. Food and Drug Administration (FDA) recently proposed a rule that would require the “medical device system” to conduct risk analyses to manage cybersecurity risk throughout the lifecycle of a medical device and its connected network. The rule language calls for a “probabilistic” model drawing on historical data, strongly suggestive of Factor Analysis of Information Risk (FAIR™).
The U.S. Food and Drug Administration (FDA) recently proposed a rule that would require the “medical device system” to conduct risk analyses to manage cybersecurity risk throughout the lifecycle of a medical device and its connected network. The rule language calls for a “probabilistic” model drawing on historical data, strongly suggestive of Factor Analysis of Information Risk (FAIR™).
An FDA press release detailed that:
“The draft guidance replaces the 2018 draft guidance and is intended to further emphasize the importance of ensuring that devices are designed securely, enabling emerging cybersecurity risks to be mitigated throughout the Total Product Life Cycle, and to outline the FDA’s recommendations more clearly for premarket submission content to address cybersecurity concerns.”
 Jacqueline Lebo is a RiskLens Risk Consultant with a background in risk management for healthcare systems.
Jacqueline Lebo is a RiskLens Risk Consultant with a background in risk management for healthcare systems.
The draft guidance dives into several topics, including:
- Cybersecurity as a Quality Systems Regulation (QSR) measure,
- Transparency in reporting any cybersecurity vulnerabilities, and
- Analyzing cybersecurity risk as a part of the premarket submission process and beyond for all medical devices.
The guidance speaks specifically to cyber risk analysis by stating that “Effective security risk management” should be addressed in a “probabilistic manner where an assessment for the likelihood of occurrence for a particular risk could be estimated based on historical data or modeling.”
What is FAIR?
FAIR is the international standard for cyber risk quantification. FAIR is compatible with frameworks such as HITRUST CSF, but unlike frameworks, a FAIR analytical platform facilitates estimation of probable risk reduction in the financial terms that business decision-makers understand, building a foundation for robust risk management – without heat maps or other imprecise communication about risk.
Learn more: FAIRCON2020 Video: How Highmark Health Combines FAIR and HITRUST for Better Cyber Risk Management
How does FAIR analysis apply to the FDA proposed rule on cybersecurity for networked medical devices
Let’s break down the guidance provided by the FDA to understand how FAIR can help meet this requirement and empower better risk-based decisions around medical device cybersecurity.
FAIR is a way to model risk scenarios or cybersecurity related failures in quantitative terms.
Say a rural hospital wants to understand its risk around a new imaging device being taken offline by a zero-day vulnerability exploited by a hacker. FAIR could help you model this risk in a way that allows you to determine how often this risk may occur and if it were to occur how much it would cost. Then it allows you to layer in controls to model how effective existing or potential controls are at mitigating the identified risk (see example below).
FAIR analysis helps to explain the probability or likelihood by using Monte Carlo simulations, much like other predictive modeling, to determine a most likely, average, minimum, and maximum value for cyber loss event probability.
This is done by using data from the industry and the organization’s internal records to model out Loss Event Frequency, or the probable frequency within a given timeframe that a threat action will result in loss, therefore answering the FDA's first concern around probability and likelihood that a risk will occur.
Learn FAIR with online training approved by the FAIR Institute
 In our example with the imaging device being taken offline by a hacker, we could model how often this event may occur in a given time frame using data about potential vulnerabilities with the device or software and industry data on threat actors.
In our example with the imaging device being taken offline by a hacker, we could model how often this event may occur in a given time frame using data about potential vulnerabilities with the device or software and industry data on threat actors.
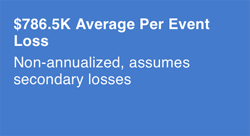 This is done by defining loss magnitude or losses incurred from the loss event itself, the results of the threat actor successfully impacting the asset. This can be done by using industry data or available internal data, such as how much it would cost to respond to this type of event, how long the imaging machine could be down, and other data to map out exactly how much this type of event would cost.
This is done by defining loss magnitude or losses incurred from the loss event itself, the results of the threat actor successfully impacting the asset. This can be done by using industry data or available internal data, such as how much it would cost to respond to this type of event, how long the imaging machine could be down, and other data to map out exactly how much this type of event would cost.
In our scenario regarding the imaging equipment, we know our loss is likely to materialize once every 2.56 years and that, on average, losses will be $786,500 per event. However, we know that we will be implementing automated vulnerability patching on the machine, and we want to show by how much that will reduce risk.
By adding that control, we reduce our loss event frequency down to roughly once every 50 years. The report below models how implementing automated patching reduces risk by 93.57%, a highly effective control for the purposes of this scenario.
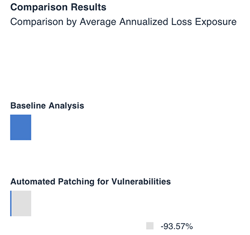 Not only does this provide valuable data for decision makers when determining how they will set up these medical devices in health systems, but it provides transparency on how effective certain controls are. This meets additional requirements detailed in the proposed rule that ask for transparency from manufacturers and usable data on how effective certain control requirements are to end users.
Not only does this provide valuable data for decision makers when determining how they will set up these medical devices in health systems, but it provides transparency on how effective certain controls are. This meets additional requirements detailed in the proposed rule that ask for transparency from manufacturers and usable data on how effective certain control requirements are to end users. Overall, the new rule brings clarity to an industry that has in the past operated in a cyber-risk grey zone. It is clear, based on the language provided in the proposed guidance that the FDA wants to see the method behind the madness and that heat maps or other qualitative outputs will no longer be acceptable ways to identify and manage cyber risk associated with medical devices.
Implication of the FDA proposed medical device rule: FAIR cyber risk analysis needed for cybersecurity for medical devices and hospital networks
Another important highlight from the proposed guidance is that the FDA realizes that in a world with so many connected devices the device manufacturer is not solely responsible for the security of the device.
That responsibility lies also with the network that supports the device, whether it be an ambulance company, a hospital network, a third-party software company, large insurance enterprise or in some cases the end user.
Specifically, the rule details that the new guidance applies to “medical device systems” (including the device and systems such as healthcare facility networks, other devices, and software update servers to which it is connected).
This would mean that a similar analysis may need to be completed across the medical device system by other parties to account for cybersecurity risk. The device manufacturer may have run this scenario and documented it in its user guide and premarket submission -- but is the small rural hospital from this scenario also aware of the risk and planning for it? Based on the proposed guidance, the FDA expects that they are. They are expecting that this type of planning be completed throughout the device’s lifecycle.
An example of when analysis may need updating is when device software is no longer supported by the company; that is, how should the hospital account for the risk associated with unknown vulnerabilities? The FDA expects that similar analyses are completed, and appropriate controls are implemented to protect the hospital and patients.
The data is available, and FAIR can help you use it to model risk to protect your medical devices and your cybersecurity environment as a whole.
The proposed rule is open for comment until July 7, 2022.









