In his post for the FAIR Institute Blog, How to Delegate Risk, Steve Poppe gives readers a great sense of how risks, expenses and budget decisions roll up. We're going to follow that to consider how risk treatment decisions are appropriated. Let’s look at it through the lens of the CISO.
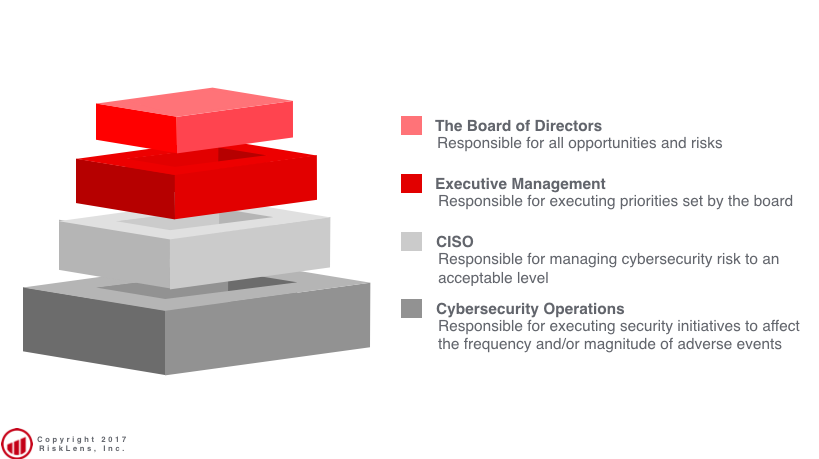
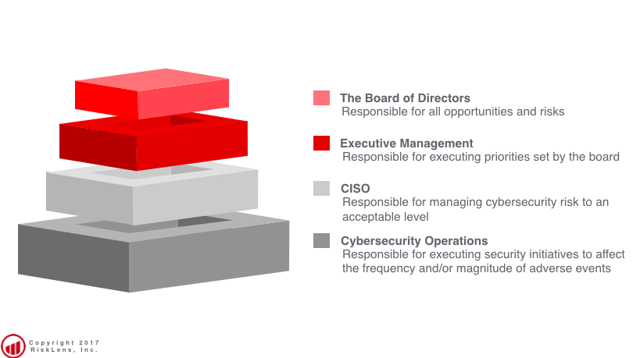
Ultimately, if we cannot prioritize cybersecurity risk effectively, Executive Management and The Board of Directors stands a snowball's chance of managing it. Part of effective prioritization is a sense of treatment options. Empowering treatment options occurs at multiple levels. For a CISO, that typically means the CTO or CIO delegates a budget which is the first structural component a CISO needs for making risk treatment decisions. The second component is provided by the Board of Directors via Executive Management with regards to opportunities and levels of acceptable risks.
Step into the shoes of the CISO
The CISO is responsible for managing cybersecurity to an acceptable level of risk without compromising growth opportunities. CISOs then empower their direct reports to make treatment decisions within their area relative to the resources available. An example of execution of this approach would be the head of an Insider Threat program implementing the data loss prevention (DLP) capabilities designed to thwart theft of sensitive customer data. This isn’t done in a vacuum; it involves prioritization activities by the CISO relative to risk treatment options in other spaces under her charge.
In a FAIR world, that decision would be evaluated using FAIR analyses and scrutinized within the context of how the new capability reduces either the likelihood of events occurring or their impact. Ultimately, the trajectory of the risk posed by adverse events involving insiders would move from an unacceptable level of risk towards the appetite (or tolerance, however your org describes it).
Executing the example initiative falls largely on the shoulders of Cybersecurity Operations; they often implement and manage these solutions over time. It’s implicit in the mission of Cybersecurity Operations to make risk treatment decisions. Again, let’s step into the example.
Once the DLP initiative is running we expect alerts on potentially illicit behavior. Those manning the station are charged with determining the quality of the information and categorizing it as inappropriate. After categorization, there is often a technical treatment capability such as shutting down access to a system, turning a system off, or locking down an account. These sorts of tactical decisions happen on a regular basis and are delegated to the Cybersecurity Operations level for two reasons:
- they’re trained analysts with discernment over their problem space
- the treatment options available to them rarely affect growth opportunities
Your mileage may vary
Across the globe, I’ve been exposed to this same framework of appropriating risk treatment capabilities. While your organization may employ more explicit guidelines for risk treatment, the same overarching approach makes sense: the further removed from the Board you are, the more risk treatment decisions become tactical. Make no mistake, those actions are still risk treatment decisions.
Related:









