How Threat Intelligence Can Help Third Party Risk Assessments

 We’ve finally arrived at the fourth and final installment in this series exploring the relationship between threat intelligence and risk management. If you’re just joining us, previous posts are listed at the bottom of the page
We’ve finally arrived at the fourth and final installment in this series exploring the relationship between threat intelligence and risk management. If you’re just joining us, previous posts are listed at the bottom of the page
(and I do encourage you to start with those before diving into this one).
We’ve covered a fair amount of ground in this series, but there’s one topic I think deserves attention before we close things out – how threat intelligence can help (save) 3rd party risk assessment.
<rant>
For those not familiar with the process of assessing and managing information risk related to 3rd parties (vendors, suppliers, contractors, partners, etc) – you’re honestly better off. Stop reading and stay as far away as you can. If you do have responsibilities in this painful-yet-important area of information risk management, I want you to know that I feel your pain and want to help. I consider 3rd party risk assessment **AS IT’S TYPICALLY DONE** to be one of the most wrecked and wasteful practices in all of information security. I realize that’s an extreme statement – and I truly don’t make it to cause offense – but I think its a valid one. A huge amount of organizational time, talent, and treasure are continually poured into this sinkhole and I see little evidence that we get much risk-reducing value out of it other than a compliance checkbox.
</rant>
Looking for monsters under the bed
Please note I am not minimizing the risk here; my research over the last 10+ years shows that 3rd parties cause or contribute to somewhere between 1 in 4 to 1 in 3 data breaches. I’m saying the way we assess and manage 3rd party risk is broken.
But don’t just take my word for it; Calvin understands my point and illustrates it well in this strip below (see what I did there?). He’s concerned about monsters under the bed and uses the tried-and-false method of self-attestation to assess the risk. Even though the assessment results show “no” risk exposure, you can see from his face that he’s not very comforted by them.

Clipped from The Essential Calvin & Hobbes, pg 155.
Now, you might be thinking “that doesn’t have much to do with 3rd party risk and, even if it did, it didn’t cost him much to do that assessment.” And you’d have a point. But as he has a knack of doing, Calvin helps us examine our grown-up issues through his six-year-old thoughts and experiences. His monster test might be trivial, but what happens when hundreds of potential “monsters” must be evaluated? And how about asking each of them hundreds of detailed questions that all require non-trivial answers? What if all of this cost real money and distracted good people from doing good things to actually reduce risk? To top it all off, what if all that effort netted results that held no more truth or usefulness than the monster’s reply above and didn’t change anything anyway? You don’t have to be a boy genius to see that something under the 3rd party risk assessment bed is drooling.
Hints of intelligence in 3rd party risk management
After all that, I should clarify that I am not writing this blog to fix 3rd party risk management. Some things even my lucky rocketship underpants can’t help. Thankfully, others are tackling various aspects of that issue. For example, BitSight rates 3rd parties using externally observable evidences of risk (like drool under the bed) instead of endless questionnaires and RiskLens focuses on their capacity to manage risk as a key factor in dealing with 3rd parties. What I’d like to do instead with our remaining time is show how threat intelligence and, more importantly, intelligence sharing can help assess the presence and size of 3rd party monsters and facilitate actions other than shouting for Mom.
In an earlier post, we used NIST’s Special Publication 800-39 as the basis of our discussion on how threat intelligence fits into the risk management process. It’s not the only risk framework out there by any stretch (we also looked at ISO/IEC 27005), but it serves as reasonable prototype. We’ll go with it again here.
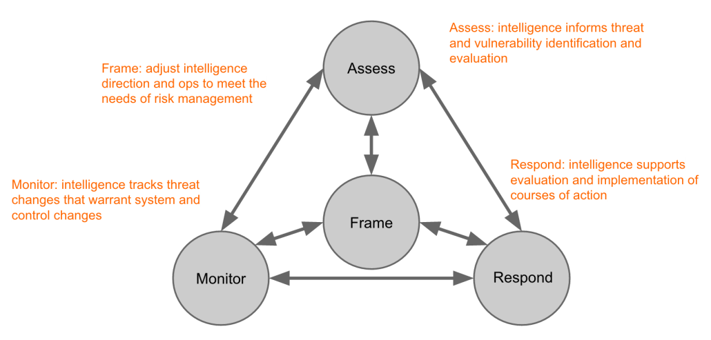
NIST SP 800-39 Risk Management Process with annotations to highlight role of threat intelligence
Not surprisingly, SP 800-39 stresses the importance of considering 3rd party risk relationships. It doesn’t specifically call out “use intel here,” but it does give a strong hint: “For organizations dealing with advanced persistent threats (i.e., a long-term pattern of targeted, sophisticated attacks) the risk posed by external partners (especially suppliers in the supply chain) may become more pronounced” (pg 8). From that, I conclude that 3rd party relationships must be considered during the intelligence direction phase and collection efforts should be adapted to include them.
One quick win here is to use threat intelligence to focus 3rd party risk assessments on what matters. Based on who the third party is, what they do, where they sit, and how they’re interacting with you, different threats will be more or less relevant than others. Threat intelligence can help these assessments be more meaningful and less costly. This could be a whole blog post on its own, but I’m going to move on to the point I’d really like to make about 3rd party risk management, which emphasizes collaboration over assessments.
I’m very glad to see this little nugget in SP 800-39: “Establish practices for sharing risk-related information (e.g., threat and vulnerability information) with external entities, including those with which the organizations have a risk relationship as well as those which could supply or receive risk-related information (e.g., Information Sharing and Analysis Centers [ISAC], Computer Emergency Response Teams [CERT]) (pg 8). Thus, intelligence ops should identify 3rd parties to include in the dissemination phase and collaborate to determine what should be shared to meet the needs of all parties. The feedback phase can help adjust and improve this over time for all involved.
Hang with me awhile more as I expound upon on the “supply chain” and “information sharing” notions presented mentioned in the above text. It’s the most important part of this post and where I see threat intelligence having the biggest impact on 3rd party risk management.
A way forward: Intelligence collaboration within supply chains
There’s nothing in SP 800-39 that prompts me to mention intelligence processing and analysis in the context of 3rd party risk management, but I’m going to bring it up anyway. The notion of “crowd-sourcing” or “peer-sourcing” intelligence is not new. Many benefit from leveraging the knowledge, tools, and talents of others for their research and operational purposes. But what about “chain-sourcing?” Rather than building walls of worthless questionnaires between partners, why not proactively collaborate to process and analyze intelligence to better manage shared risks?
A supply chain – or value chain as they’re sometimes called – is essentially a group of organizations working together to bring goods and services to market. A highly-collaborative group of 3rd parties, if you will. The field of supply chain management understands well that risk to one represents risk to the whole. A very rich body of research and practice recognizes the value of collaboration and information sharing to reduce traditional supply chain risk by getting the right products to the right place and the right time. I think it’s high time we realize that intelligence collaboration can do the same for cybersecurity risk.
Lemme use some data to make my case. The figure below comes from a source near and dear to my heart, the Verizon’s 2015 Data Breach Investigations Report. It uses a clustering algorithm to place industries with similar threat profiles in proximity to one another. The DBIR explains it well:
“Each dot represents an industry “subsector” (we chose to use the three-digit NAICS codes—rather than the first two only—to illustrate more specificity in industry groupings). The size of the dot relates to the number of incidents recorded for that subsector over the last three years (larger = more). The distance between the dots shows how incidents in one subsector compare to that of another. If dots are close together, it means incidents in those subsectors share similar VERIS characteristics such as threat actors, actions, compromised assets, etc. If far away, it means the opposite. In other words, subsectors with similar threat profiles appear closer together.”
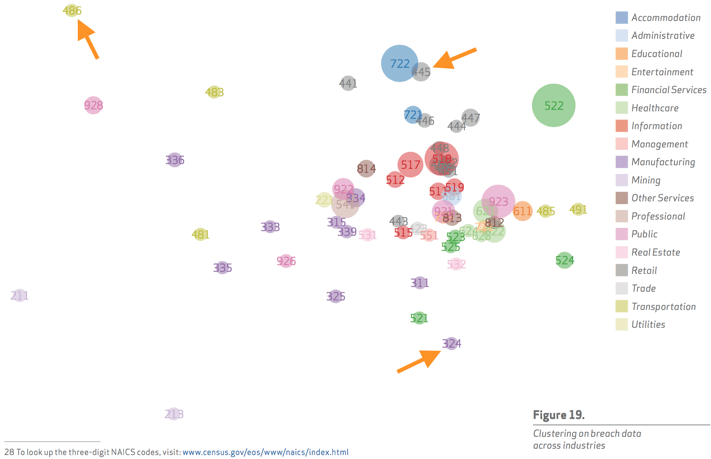 I’ve added the orange arrows to demonstrate what happens when you join different types of organizations into a supply chain that must be highly collaborative and coordinated to remain competitive. A very basic supply chain will have a manufacturer, a distributor (some type of transportation), and retailer. Notice in the figure how the Manufacturing subsector 324, Transportation subsector 486, and Retail subsector 445 basically form a triangle of points about as far as you can get from each other. That means their threat profiles are very, very different. When those organizations connect systems and processes to form supply chain, you can imagine that they’re exposing each other to threats the other party has never seen before. Kinda like sharing toothbrushes. Questionnaires won’t fix that. A collaborative approach to threat intelligence and defense is the only way forward I see to efficiently and effectively manage risk for all parties.
I’ve added the orange arrows to demonstrate what happens when you join different types of organizations into a supply chain that must be highly collaborative and coordinated to remain competitive. A very basic supply chain will have a manufacturer, a distributor (some type of transportation), and retailer. Notice in the figure how the Manufacturing subsector 324, Transportation subsector 486, and Retail subsector 445 basically form a triangle of points about as far as you can get from each other. That means their threat profiles are very, very different. When those organizations connect systems and processes to form supply chain, you can imagine that they’re exposing each other to threats the other party has never seen before. Kinda like sharing toothbrushes. Questionnaires won’t fix that. A collaborative approach to threat intelligence and defense is the only way forward I see to efficiently and effectively manage risk for all parties.
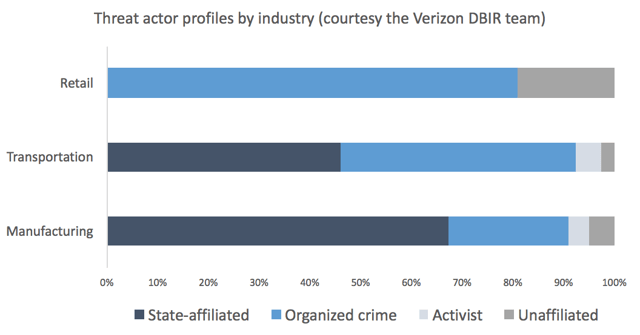
To provide another view on the same concept, I used my “phone a friend” card to request some additional data from the Verizon DBIR team. They graciously agreed, and @gdbassett whipped up some R code to generate the stats behind the chart below (don’t blame him for the chart itself; that’s my fault). It shows the percentage of breaches attributed to several common varieties of threat actors for the three industries highlighted above. You’ll notice stark differences among them with respect to threat actor profile. Retail is hammered by organized criminal groups, while state-affiliated actors plague Manufacturing. Transportation suffers fairly equally from both. This reinforces the point from above – if organizations from these sectors are sharing threats, so-to-speak, as supply chain, then they need to be sharing what they know about those threats and helping each other to defend against them.
As the concept of Information Sharing and Analysis Organizations (ISAOs) evolve, I hope to see info/intel sharing groups form around supply chains rather than industries. I hope I’ve made the point that such relationships arguably have stronger incentives to share intelligence than non-collaborating industry peers, and I can see this building momentum for cooperative defense. Plus, supply chains already have a need to share and a basis for trust established, which will ease many intel sharing paint points. I think this concept holds a lot of promise and I look forward to helping a supply chain deploy ThreatConnect to help its members coordinate threat intelligence operations.
Aaaaannnnnd we’re done here
Thanks to all of you who have hung with me in this four-post series. I was glad for the opportunity to organize some of my thoughts on “paper,” and I hope they’re of some practical use to you as you seek to use threat intelligence to inform and improve risk management in your organization.
Post 1: Introduction to Threat Intelligence and Risk Management
Post 2: How Threat Intelligence Fits Within Risk Management
Post 3: How Threat Intelligence Can Drive Risk Analysis
This post was originally published on threatconnect.com









