How to Factor Worst-Case Cyber Events into Risk Analysis - Jack Freund on the Cyentia "Xtreme" Report

 All end-user devices destroyed at shipping company Maersk by the NotPetya malware…Dating site Ashley Madison cancelling its IPO after a data breach…Equifax fined $1.7 billion for its negligence in a breach. Extremely high-impact cyber events -- out at the 95th percentile on a FAIR™ analysis loss exceedance curve – do happen and, as a report from the Cyentia Institute finds, with surprising regularity. The IRIS 20/20 Xtreme study examined the 100 largest cyber loss events of the past 5 years and found:
All end-user devices destroyed at shipping company Maersk by the NotPetya malware…Dating site Ashley Madison cancelling its IPO after a data breach…Equifax fined $1.7 billion for its negligence in a breach. Extremely high-impact cyber events -- out at the 95th percentile on a FAIR™ analysis loss exceedance curve – do happen and, as a report from the Cyentia Institute finds, with surprising regularity. The IRIS 20/20 Xtreme study examined the 100 largest cyber loss events of the past 5 years and found:
- A median loss of $47M, with one-in-four exceeding $100M and five events at $1 billion or more in losses.
- 27 events were reported in SEC filings, 25 triggered executive changes, and 23 a government inquiry
- 43% of all monetary losses were attributable to nation-state threat actors
What should FAIR analysts make of these findings? Jack Freund, PhD, co-author of the FAIR book, a FAIR Institute fellow and Head of Methodology at VisibleRisk, collaborated with Cyentia on the report and gave this advice:
Q: What is the practical use of the data here which are, to some extent, about black swans, low frequency, very high impact?
A: If anything, I’ll say it’s a refutation against the notion that these events are black swans. Rare though they may be, they are certainly foreseeable.
This is the kind of thing that you need when you’re trying to build your loss ranges to account for those 95thpercentile or near worst-case kind of things. The report looks at all events with an aggregate loss of over $20 million dollars. So, this is definitely within striking range for a lot of organizations but perhaps not high frequency events.
Q: How does the report help with building out loss ranges?
A: We purposefully categorized the losses using FAIR terminology. You’ll see things like response cost, productivity, fines and judgments, so it’s tailor-made for risk analysts who are looking to better inform their FAIR analyses.
Q: What did the report find in terms of materiality, and what companies reported on?
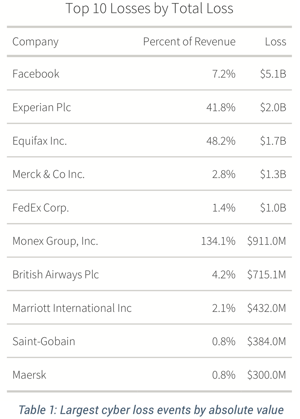 A: Materiality is a fascinating concept for cybersecurity events. It’s difficult to be able to build a universal, quantitative, percent type threshold unless you have some way to index it back to meaningful numbers for that company. Materiality is one of the ways that you can do that. The Cyentia Report computes that for these organizations.
A: Materiality is a fascinating concept for cybersecurity events. It’s difficult to be able to build a universal, quantitative, percent type threshold unless you have some way to index it back to meaningful numbers for that company. Materiality is one of the ways that you can do that. The Cyentia Report computes that for these organizations.
Now, the interesting thing is, the size of a fine alone can be dwarfed by companies’ materiality based on a revenue benchmark. The $5 billion Facebook fine, is only 7.2% of revenue.
A couple notches down on that list, you have an Equifax fine of $1.7 billion, which is 48.2% of revenue for the year it was assessed. So, for a lot of organizations, looking in terms of percent of revenue is a good way to go on materiality.
One feature I like to call out in this report is that some of the more costly incidents actually happened because they were involved in cryptocurrency exchanges: lost wallets and stolen cryptocurrency. It’s a reminder to make sure loss events that you’re incorporating into your range estimation filter out the activities you’re not into.
Q: The study showed that a surprising amount of this activity was generated by nation-state actors. Should lower-profile companies be factoring more in their calculations for nation states as threat actors?
A: I don’t know that we can say for certain that these are targeted nation-state attacks. I think these are broad-based attacks. Ransomware events run by North Korean state actors or similar are more opportunistic.
With FAIR, we do have a way of differentiating between opportunistic attacks vs targeted attacks. So, while the skillset and the resources that they can bring to bear in the threat capability side will be significantly increased, you’re also going to see a change in frequency, as you move from targeted attacks to opportunistic attacks, so I think that changes the calculus a little bit on the risk side for thinking about those types of threat actors.
Q: What’s your advice on how to talk to boards of directors about the likelihood of these kinds of events?
A: It’s important, as always, to be careful you are not playing Chicken Little. Referencing these types of events is different than referencing most likely events. Using a FAIR loss curve with a mode [or most likely] and a 95thpercentile point is helpful to characterize the overall type of things that could happen.
 But we’re always talking about future events in risk analysis, so this allows us to say most likely maybe it’s $250,000 and maybe we can eat that but there’s a non-zero percentage of the time that we’re going to have an event where we could lose 15-20-30 million dollars – and what are we going to do if that happens?
But we’re always talking about future events in risk analysis, so this allows us to say most likely maybe it’s $250,000 and maybe we can eat that but there’s a non-zero percentage of the time that we’re going to have an event where we could lose 15-20-30 million dollars – and what are we going to do if that happens?
Are there ways that we can reduce the likelihood of that happening by increasing our security hygiene? Are there ways that we can help our balance sheet absorb that kind of loss when it does happen, maybe once every 10, 15 or 20 years? Do we buy cyber insurance to help offset that? Do we set aside money for a rainy day?
These things focus on decision making that CISOs want to involve their team and their leadership with. You shouldn’t manage your daily risks based on that 95th percentile, but it’s important to have perhaps a second planning session with key people in your organization to think about worst-case examples.
Related:
Drawing FAIR™ Conclusions from Cyentia’s Information Risk Insights Study (IRIS)









