Mapping FAIR-CAM to Cybersecurity Frameworks: ‘Compliance Is Going to Radically Change’
Hat tip to the members of the FAIR Institute who have done so much to develop FAIR™ as the standard for quantitative cyber risk analysis – and a special recognition medal to the team of volunteers who mapped the new FAIR-CAM controls analytics model to the leading cybersecurity controls frameworks, including CIS, NIST CSF, NIST 800-53, FFIEC, MITRE ATT&CK and ISO 27002.
As team member Tyler Britton said, it was a process of “slogging through hundreds of controls,” to put in the “mental effort” of interpreting what each control does to affect risk, working with “control frameworks that have not really been developed with how they address risk in mind,” said Daniel Stone.
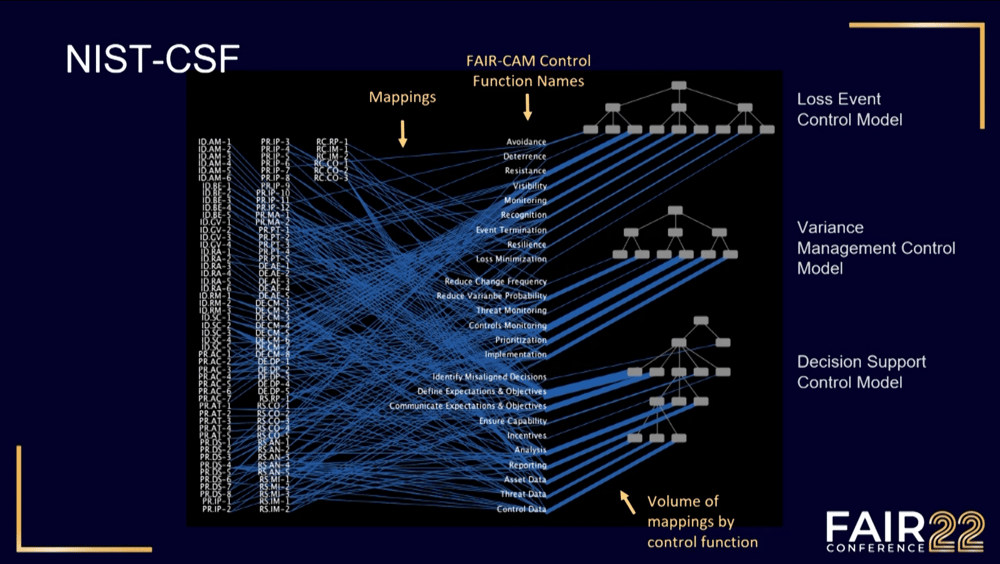
To get an idea of the mental effort, just look at the mapping in this image, with the NIST CSF control families on the left connected by spiderwebs to their functions in risk reduction as described by FAIR-CAM on the right.
The mapping team discussed the project in a session at the recent FAIR Conference (FAIRCON22), led by FAIR-CAM creator Jack Jones.
Panel: Mapping Leading Control Frameworks to FAIR-CAM™
Moderator: Jack Jones, Chairman, FAIR Institute
Daniel Stone, Associate Director, Security & Privacy, Protiviti
Erin Macuga, Manager, Risk and Information Security, Thrivent Financial
Robert Immella, Global Leader of Cyber Risk Quantification, Caterpillar Inc
Tyler Britton, Quantitative Cyber Risk Manager, Dropbox
Drew Brown, Information System Security Developer, FAA
Watch the video of the presentation now (FAIR Institute Contributing Membership required. Become a member.)
To recap, FAIR-CAM is a model that:
>>Categorizes controls by type and function
>>Sets them in relation to each other, clarifying their interplay
>>Accounts for the direct and indirect effect of controls on risk
>>Assigns units of measurement for control performance enabling a quantitative approach for reliable analysis of the effectiveness of controls and controls systems.
See the FAIR-CAM documentation
Jack Jones discussed FAIR-CAM in another session at FAIRCON22.
Why map cyber controls frameworks to FAIR-CAM?
First to fulfill a longtime goal of the FAIR movement – to make compliance with frameworks a meaningful exercise in mitigating risk rather checking boxes on a list. As Drew Brown said, “Compliance is going to radically change. An assessor comes in and asks does the control exist and is it functioning the way it’s supposed to? Now we know. We can actively measure and document if that control is doing what it supposed to do. Now when we get that audit finding we can answer if it is really a big deal or something we can work on in the next fiscal year”
“The other piece of it is scale,” said Daniel. “We can’t do that without the language and modeling behind automation. There needs to be more research done on control efficacy. But FAIR-CAM provides the language behind how we can use those models to scale in a way that’s documented, clearly defendable and open.”
At this stage of development, the panel participants agreed, FAIR-CAM hasn’t hit the automation stage but is immediately valuable as a thought and communication exercise. Tyler Britton said that he recently met with his organization’s audit and compliance team and “they are very interested in using this to have better conversations (on risk) and not just be the police all the time…because it does provide a common ground. If they find ten control gaps, we have better language to talk about which ones should be prioritized. That was a really positive thing that happened already.”