Meltdown, Spectre, Heartbleed - Risk Modeling the Vulnerability du Jour, Part 1: Framing

 Every few months or so, we hear about a widespread vulnerability or cyber attack that makes its way to mainstream news. Some get snappy nicknames and their very own logos, like Meltdown, Spectre, and Heartbleed. Others, like the Sony Pictures Entertainment, OPM, and SolarWinds attacks cause a flurry of activity across corporate America with executives asking their CISO’s and risk managers, “Are we vulnerable?”
Every few months or so, we hear about a widespread vulnerability or cyber attack that makes its way to mainstream news. Some get snappy nicknames and their very own logos, like Meltdown, Spectre, and Heartbleed. Others, like the Sony Pictures Entertainment, OPM, and SolarWinds attacks cause a flurry of activity across corporate America with executives asking their CISO’s and risk managers, “Are we vulnerable?”
Tony Martin-Vegue co-chairs the San Francisco Chapter of the FAIR Institute and is Senior Information Security Risk Engineer at Netflix. Tony was honored with the FAIR Institute’s FAIR Ambassador Award at the 2020 FAIR Conference in recognition of his longtime advocacy for FAIR. This post originally appeared on Tony’s blog about risk management.
I like to call these the vulnerability du jour, and I’m only half sarcastic when I say that. On the one hand, it’s a little annoying how sensationalized these are. Media-worthy vulnerabilities and attacks feel interchangeable: when one runs its course and attention spans drift, here’s another one to take its place, just like a restaurant’s soup of the day. On the other hand, if this is what it takes to get the boardroom talking about risk - I’ll take it.
When the vulnerability du jour comes on an executive’s radar, the third or fourth question is usually, “Was this on our risk register?” Of course, we don’t have crystal balls and can’t precisely predict the next big thing, but we can use brainstorming and thought exercises to ensure our risk registers are well-rounded. A well-rounded and proactive risk register includes as many of these events and vulnerabilities as possible - on a high level.
This is a two-part series, with this post (part 1) setting some basic guidelines on framing these types of risks. Part 2 will give brainstorming ideas on how to turn your risk register into one that’s forward-looking and proactive instead of reactive.
Building a forward-looking risk register means you’re holding at least annual emerging risk workshops in which you gather a cross-section of subject matter experts in your company and brainstorm any new or emerging risks to fill in gaps and blind spots in your risk register. I have three golden rules to keep in mind when you’re holding these workshops.
Golden Rules of Identifying Emerging Risk
#1: No specifics
We’re forecasters, not fortune tellers (think a meteorologist versus Miss Cleo). I don’t think anyone had “State-sponsored attackers compromise SolarWind’s source code build system, leading to a company data breach” in their list of risks before December 2020. (If you did - message me. I’d love to know if Elvis is alive and how he’s doing.)
Keep it high-level and focused on how the company can prepare for resiliency rather than a specific vector or method of attack. For example, one can incorporate the SolarWinds incident with a generalized risk statement like the example below. This covers the SolarWinds vector and other supply chain attacks and also provides a starting point to future-proof your risk register to similar attacks we will see in the future.
Attacker infiltrates and compromises a software vendor's source code and/or build and update process, leading to company security incidents (e.g. malware distribution, unauthorized data access, unauthorized system access.)
The fallout from the incident can be further decomposed and quantified using FAIR’s 6 forms of loss or a similar model.
#2: Risk Quantification
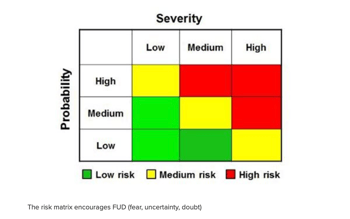 Communicating hypothetical, speculative, or rare risks is hard to do without scaring people. If a good portion of your company’s risk register is stuff like hypervisor escapes, privilege escalation via rowhammer, and state-sponsored attacks you really need to have the data to back up why it needs executive attention. Otherwise, it will just look like another case of FUD.
Communicating hypothetical, speculative, or rare risks is hard to do without scaring people. If a good portion of your company’s risk register is stuff like hypervisor escapes, privilege escalation via rowhammer, and state-sponsored attacks you really need to have the data to back up why it needs executive attention. Otherwise, it will just look like another case of FUD.
The key to success is risk quantification: risk articulated in numbers, not colors. A bunch of red high risks (or green low risks) obfuscates the true story you are trying to tell.
All risk, because it’s forward-looking, is filled with uncertainty.
Unique and exotic risks have even more uncertainty. For example, there have been so many data breaches that we have a really good idea of how often they occur and how much it costs. Supply chain attacks like SolarWinds? Not so much. Choose a risk model that can communicate both the analyst’s uncertainty and the wide range of possibilities.
I use FAIR because it’s purpose-built for information and operational risks but you really can use any quantitative model.
#3: Be aware of risk blindness
 Every good risk analyst knows the difference between risks that are possible and those that are probable. Without going too deep into philosophy, just about anything is possible and it’s the risk analyst’s job to rein in people when the risk brainstorming veers to outlandish scenarios. But, don’t rein them in too much!
Every good risk analyst knows the difference between risks that are possible and those that are probable. Without going too deep into philosophy, just about anything is possible and it’s the risk analyst’s job to rein in people when the risk brainstorming veers to outlandish scenarios. But, don’t rein them in too much!
Any risk, no matter how routine, was unique and a surprise to someone once upon a time. Ransomware would sound strange to someone in the 1970’s; computer crime would be received as black magic to someone in the 15th century.
Try to put yourself in this mindset as you hold emerging risk workshops. I personally love holding workshops with incident responders and red teamers - they have the ability to think outside of the box and are not shy about coming up with hypotheticals and highly speculative scenarios. Don’t discourage them. Yes, we still need to separate out possible from probable, but it is an emerging risk workshop. See what they come up with.
Next Up
I hope this post got you thinking about how to add these types of risks to your register. In part 2, I’m going to give real-life examples of how to further brainstorm and workshop out these risks.
Read Part 2 in the series, learn how to create a forward-looking risk register.









