NIST CSF 2.0 Takes a Major Step to Recognizing Cyber Risk as Business Risk
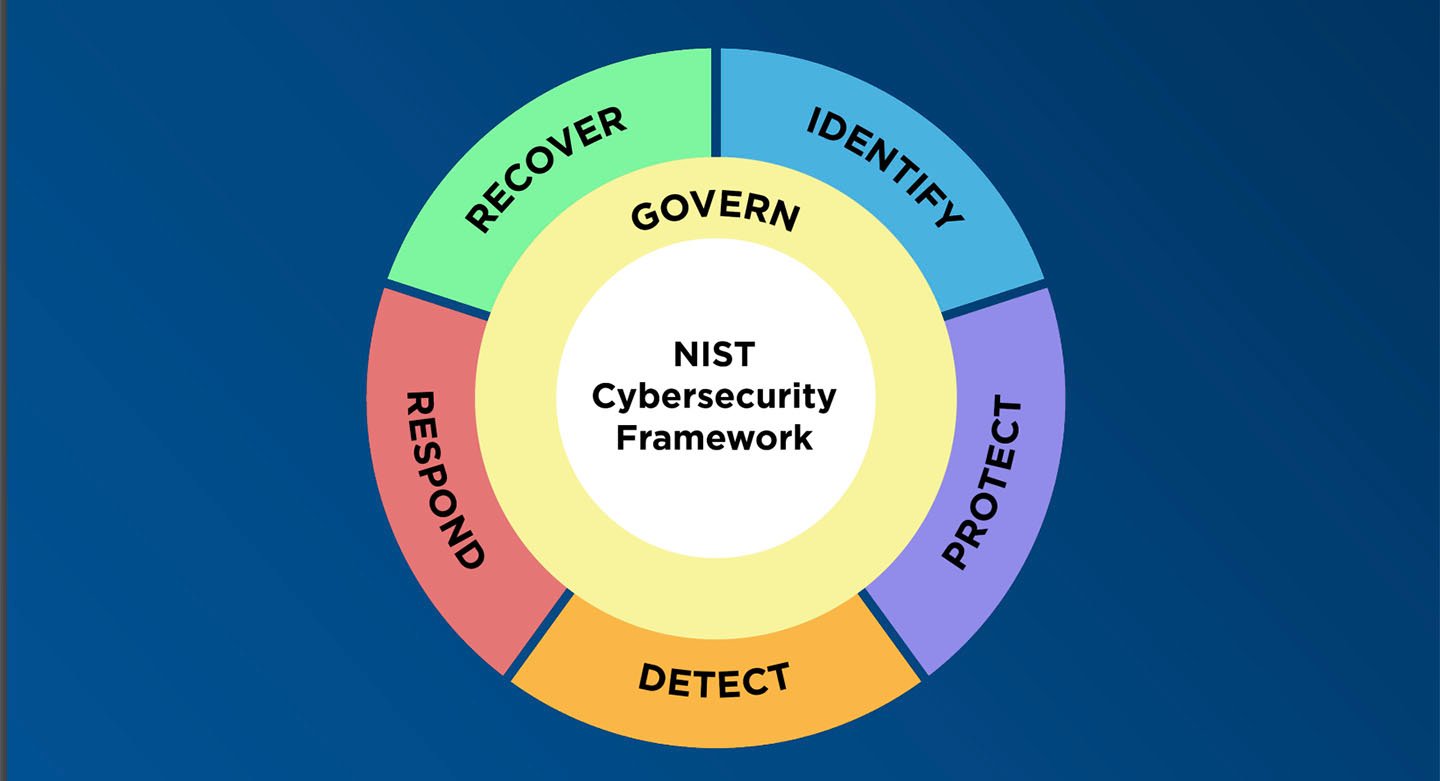
The National Institute of Standards and Technology (NIST) recently introduced the NIST CSF 2.0 update to its popular cybersecurity framework -- and firmly placed cyber risk as business risk with the addition of the Govern function to the original five pillars.
As the home of Factor Analysis of Information Risk (FAIR™), the standard for quantifying cyber risk in the economic language of business, the FAIR Institute welcomes this framework update as an important step forward for the cyber risk management profession.
 Nick Sanna is President of the FAIR Institute
Nick Sanna is President of the FAIR Institute
The NIST CSF launched ten years ago as a guide for critical industries, and long had a strictly technical approach focused on security controls. The FAIR community viewed the framework as an excellent list of best security practices, but little guidance for empirically measuring and prioritizing risk remediation efforts in a business context.
Then, in 2019, the mapping of FAIR to the CSF as an Informative Resource for defining and measuring cyber risk, confirmed that risk and security teams can confidently employ FAIR quantitative risk management alongside the other NIST CSF framework activities.
The New Govern Function in NIST CSF
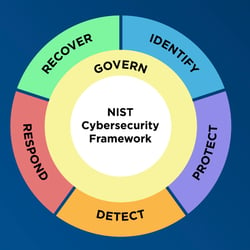 NIST added Govern as the first of the six functions (the original five were Identify, Protect, Detect, Respond, and Recover), defined as “The organization’s cybersecurity risk management strategy, expectations, and policy are established, communicated, and monitored.”
NIST added Govern as the first of the six functions (the original five were Identify, Protect, Detect, Respond, and Recover), defined as “The organization’s cybersecurity risk management strategy, expectations, and policy are established, communicated, and monitored.”
In effect, NIST lifted cybersecurity risk to a board level, whole-of-business concern. That’s very much in line with the direction of trends in corporate governance, such as the NACD Director’s Handbook on Cyber-Risk Oversight, and regulation, notably the new rules from the Securities and Exchange Commission mandating disclosure of practices and processes for cyber risk management. (Read What the New SEC Regulation on Cyber Reporting Means for the Risk Management Profession.)
Key points about the Govern function from the NIST CSF 2.0 Resource and Overview Guide:
>>Understand and assess specific cybersecurity needs.
“Determine your organization’s unique risks and needs. Discuss the current and predicted risk environment and the amount of risk your organization is willing to accept.”
Top risk assessments are a staple for FAIR practitioners, identifying risks that are both the highest probability of occurrence and cost of impact. With risk quantified in dollar terms, organizations can make informed choices on risk treatment and acceptance.
>>Develop a tailored cybersecurity risk strategy
“This should be based on your organization’s specific cybersecurity objectives, the risk environment, and lessons learned from the past and from others.”
FAIR quantitative methods enable organizations to set specific financially-oriented objectives for risk reduction, track progress and benchmark against industry averages.
>>Implement continuous oversight and checkpoints
“Analyze risks at regular intervals and monitor them continuously (just as you would with financial risks).”
The latest FAIR-powered risk management platforms process asset, controls and threat data in real-time, and perform automated risk analyses, enabling continuous cyber risk monitoring.
>>Establish and monitor cybersecurity supply chain risk management
“Establish strategy, policy, and roles and responsibilities — including for overseeing suppliers, customers, and partners.”
As recent hacks have painfully demonstrated, an organization’s cyber risk posture is very dependent on the security of its supply chain partners. The NIST CSF 2.0 now clearly states that effective cyber risk management strategies must integrate first and third party risk.
Looking Forward on Cyber Risk Management and the NIST CSF
The FAIR Institute has been actively engaged in suggesting improvements to the Cybersecurity Framework. We made several other recommendations that have not been included in this version 2.0, such as urging NIST to align the framework with FAIR-CAM, the FAIR Controls Analytics Model. “There is now a way to empirically measure control efficacy and risk reduction value,” the Institute wrote to NIST, and “define measurement scales for each of the elements in the framework to reduce ambiguity and improve quality of benchmarking and measurement.” The Institute completed a major initiative to map FAIR-CAM to the CSF (see Mapping FAIR-CAM to Cybersecurity Frameworks: ‘Compliance Is Going to Radically Change’).
Looking forward to even more improvement in the NIST CSF shouldn’t detract from the significance of 2.0 that aligns with many of our recommendations to more closely support a risk-based approach to cybersecurity versus a predominantly compliance approach. We hope the profession treats it as a guidepost to adopt foundational cyber risk management and governance practices.









