Connecting Threat Intel to Risk with MITRE ATT&CK and FAIR

“The idea is to bridge the gap between the security team and the risk team and create an environment so they can work together,” Vidit Baxi of Safe Security, the technical adviser to the FAIR Institute, told a session at the recent FAIR Conference (FAIRCON23). The bridge joins MITRE ATT&CK, the knowledge base and framework of threat actor tactics and techniques, with Factor Analysis of Information Risk (FAIR), the model for quantifying cyber risk in financial terms.
Watch the video: Connecting Threat Intel to Risk with MITRE ATT&CK and FAIR
Panelists (left to right in the photo)
Vidit Baxi Co-Founder and CISO, Safe Security
Jon Baker, Co-Founder and Director, Center for Threat Informed Defense, and FAIR Institute Board Director
Arvin Bansal, vCISO, Fortune500
(A FAIR Institute membership required to view. Join now!)
Key Takeaways of the FAIRCON23 Presentation:
 1. MITRE ATT&CK is no longer just a catalog of attacker tactics; it’s now the foundation of “threat-informed defense,” Jon Baker explained, “the systematic application of deep technical understanding of adversary tradecraft and technology to improve defenses.” Cybersecurity teams can draw on the knowledge base to simulate attacks, for instance by a threat actor like the Conti gang, following along the attack flow and evaluating their defenses at each phase.
1. MITRE ATT&CK is no longer just a catalog of attacker tactics; it’s now the foundation of “threat-informed defense,” Jon Baker explained, “the systematic application of deep technical understanding of adversary tradecraft and technology to improve defenses.” Cybersecurity teams can draw on the knowledge base to simulate attacks, for instance by a threat actor like the Conti gang, following along the attack flow and evaluating their defenses at each phase.
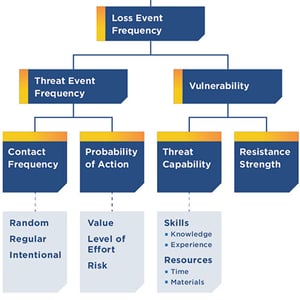
2. MITRE ATT&CK’s attack flow is a big help to FAIR analysis which runs on risk scenarios. “Attack flow can help you visualize the path” of an attacker, Vidit said, to focus a scenario and direct your attention to the factors you need to quantify to achieve accurate analysis on the Loss Event Frequency side of FAIR.
Those factors are:
- Contact Frequency (by an attacker)
- Probability of Action (by an attacker)
- Threat Capability (of an attacker)
- Resistance Strength (of your controls)
(Take a look at the full FAIR model here.)
For example, if you run up against a group that can competently execute 40 techniques from MITRE ATT&CK, you can confidently rate their Threat Capability as high, Vidit said.
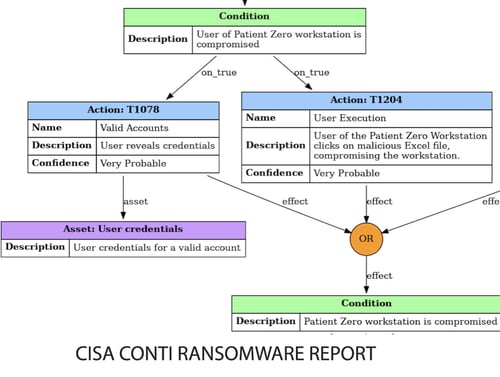
Bringing MITRE ATT&CK and FAIR together for a Business Decision on Ransomware
Arvin Bansal demonstrated how a Fortune 10 healthcare company quickly moved from 1) picking up signals of a Conti ransomware attack by threat group Wizard Spider through 2) MITRE ATT&CK analysis to 3) quantifying the FAIR factors (using the FAIR Institute’s free FAIR-U tool) to 4) making a case to business leaders to invest in protective measures based on ROI for risk reduction. And with automation of FAIR risk management now underway, risk managers can look forward to having a “pipeline” that would constantly update scenarios with live threat-informed defense data, Vidit said.
Watch the video: Connecting Threat Intel to Risk with MITRE ATT&CK and FAIR
(A FAIR Institute membership required to view. Join now!)









