 The foundation of any good risk analysis is the rationale -- the documentation of the thought process driving the ranges you selected for analysis with the FAIR model.
The foundation of any good risk analysis is the rationale -- the documentation of the thought process driving the ranges you selected for analysis with the FAIR model.
At the FAIR Institute breakfast during the last Gartner Security and Risk Management Summit, Robert Immella, FAIR cyber risk analyst for KeyBank, gave a talk filled with tips for anyone wanting to stand up their own risk quantification program (watch the video). A significant aspect of his session was all about rationale.
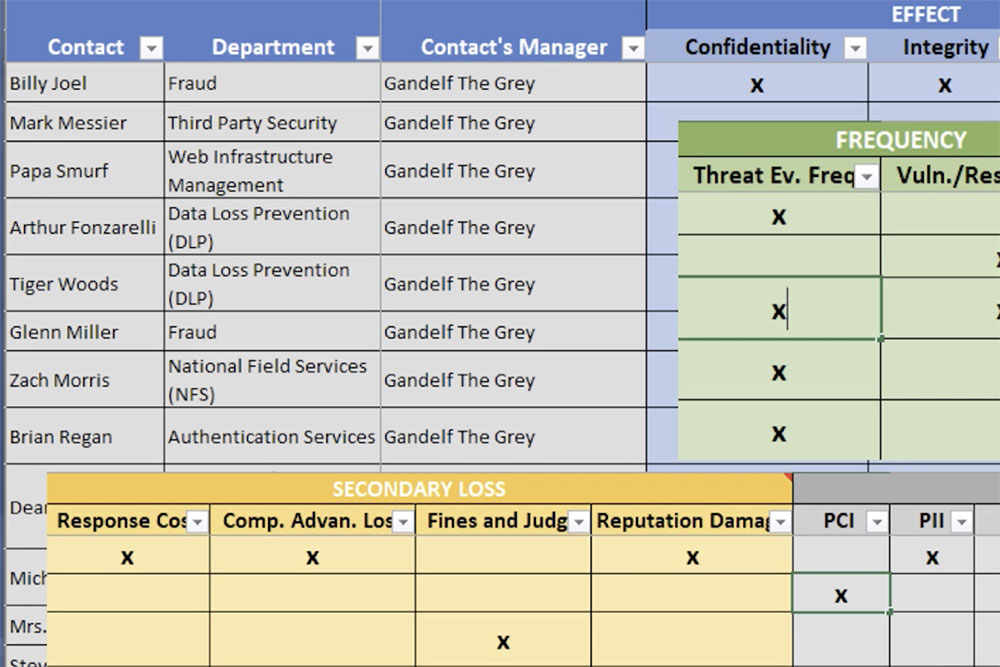
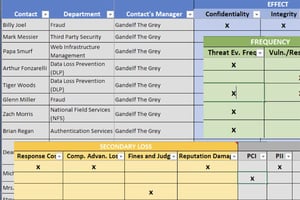
Rob first discussed that, when collecting data for a risk quantification from various subject matter experts (SMEs) and data sources there will be followup questions and list items to come back into focus at later dates. While you are compiling the laundry list of followups in your head, you may think there is no way you will forget any of these items. Well, as the list grows things will likely slip through the cracks. In order to address this issue Immella shared his template to help organize follow-up items. See below - click for a larger image.
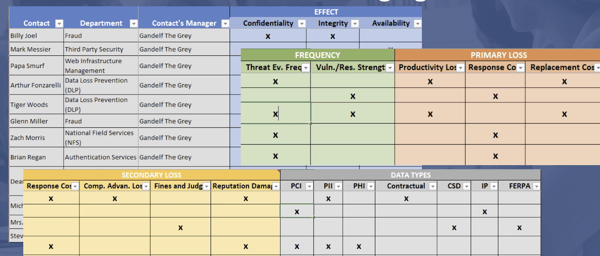
Rob’s template specifies the contact persons for any data point, their departments, their managers, and which part of the FAIR model they will have data on. Having a template similar to this will help you keep track of all sources used in a quantification, ensuring that you take into account all possible data and do not overlook any data points.
Rob not only shared his expertise on how he organizes data points for any risk quantification, but how to include these data points into your final rationale in RiskLens or other tracking system.
It is important to diligently and explicitly document:
-
The name and title of the person who gave you the estimate
-
The data they used to inform the estimate (historical events, logs, external sources, etc.)
-
Controls considered
-
Any sources of remaining uncertainty
-
Any equations used to derive your range
Even if your equation is as simple as “2 + 2 = 4”, document it in the rationale. When you or a colleague are looking back on a risk quantification, having explicit documentation on the step-by-step process that was taken to derive the final range is essential. Without clear and detailed rationale, there is room to compare apples to oranges, and your quantification will become meaningless.
Unless you have a photographic memory, rationale is the only way you are going to remember the important details of your estimates. Failing to do so may make follow-up questions difficult or impossible and it harms the credibility of your analysis if you are unable to defend your estimates.
More Tips on Data Gathering for FAIR Cyber Risk Quantification
 When Talking to SMEs, Talk Their Language
When Talking to SMEs, Talk Their Language
Instead of asking about “vulnerability” (in the FAIR model, the probability that a threat event will become a loss event), ask “What’s the likelihood of privileged insiders getting customer data from the XYZ data base?” Educate them a little bit on FAIR but you still need to speak to them in their language even if it’s technical and with respect to their asset.
from 3 Tips on How to Talk to SMEs about Cyber Risk Quantification
Rely on Calibration to Set and Document Ranges
Use calibration to help subject matter experts provide usefully precise ranges with 90% confidence.
If you ask a subject matter expert the question “how often do we see attempts by cyber criminals to breach the customer data contained in database x?” and they respond with "between once in fifty years and ten times per year" then the odds are they are probably accurate, but is that usefully precise? On the other hand, if they respond with "3.7", is that accurate? Using calibration, you can help the subject matter expert provide a range that is both usefully precise and accurate.
from 4 Tips to Reality-Check a FAIR Quantitative Risk Analysis
Always Stick to the Scope in Documenting Your Rationale
Scoping is the necessary first step in FAIR analysis in which you define the risk (or loss event, in FAIR terms).
You start with identifying the:
-
Asset at risk. For instance, the data in the database.
-
Threat actor, such as a company employee who’s careless about emailing data.
-
Impact you’re worrying about – loss of confidential data, for example.
And you end up with a risk statement that directs the rest of the analysis process. Scoping forces you to be specific in your problem to solve.
from In a FAIR Risk Analysis, Don't Collect Data till You Scope
Learn more: What Makes a Good Risk Analyst?









