
Factor Analysis of Information Risk (FAIR) has emerged as the standard Value at Risk (VaR) framework for cybersecurity and operational risk.
The FAIR Institute is a non-profit professional organization dedicated to advancing the discipline of measuring and managing information risk.
It provides information risk, cybersecurity and business executives with the standards and best practices to help organizations measure, manage and report on information risk from the business perspective. The FAIR Institute and its community focus on innovation, education and sharing of best practices to advance FAIR and the information risk management profession.

Jul 25, 2024 2:36:16 PM
Making the switch to quantitative risk management? You’ve come to the right place, the 2024 FAIR Conference (FAIRCON24), annual meeting of the FAIR community, hosted by the FAIR Institute in Washington, DC., with two days of training sessions and two days of speakers that will – we guarantee – start you off with skills and inspiration to lead your organization to cyber and operational risk management that better align with your organization’s goals.

Jul 22, 2024 10:23:00 AM

Jul 17, 2024 5:35:45 PM
It has become very apparent that there is a current challenge in the cyber risk management industry: namely, that first-party and third-party risk are siloed and often approached fundamentally differently.

Feb 15, 2023 5:09:00 PM
I recently had a conversation with clients around a risk analysis they conducted and noticed as they walked me through it that they seemed to get hung up on the terms “inherent risk” and “residual...
Read More >>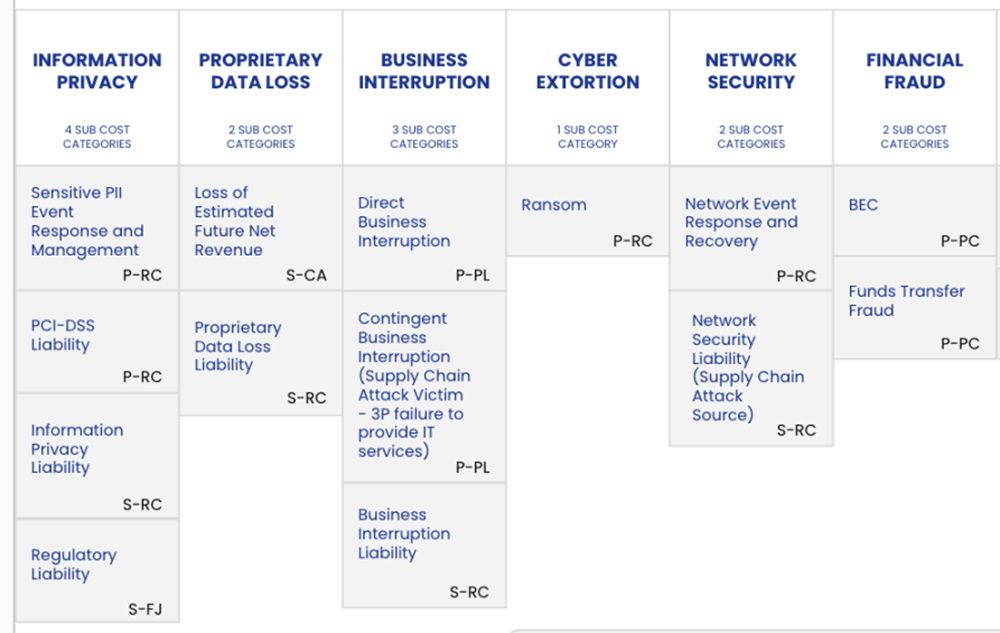
Aug 15, 2023 11:00:57 AM
The FAIR Institute has released the FAIR Materiality Assessment Model (FAIR-MAM™), a significant new ancillary standard to Factor Analysis of Information Risk (FAIR™) that provides a more detailed...
Read More >>
May 18, 2022 11:07:03 AM
If you’re looking to try Factor Analysis of Information Risk (FAIR™) in a lightweight way, these tools and resources will get you started – all of them offered by the FAIR Institute or shared by...
Read More >>