3 Steps to Combine MITRE ATT&CK and FAIR to Focus Cyber Risk Management
The MITRE ATT&CK framework is a tool used by many cybersecurity teams to help analyze adversarial attacks and techniques. By tracking adversary methods and styles of attack, organizations gain the ability to understand their cyber risk landscape from the threat actor’s perspective. Pairing MITRE ATT&CK with FAIR™, cyber risk analysis can help organizations also prioritize risk management initiatives.
Here’s how to combine MITRE ATT&CK and FAIR in 3 steps:
1. Use MITRE ATT&CK to Scope Scenarios
Before we begin our risk analysis, we have to understand what scenarios are plausible to our organization. We need to identify who are the likely threat actors, how they would access the system, what kinds of assets they would infiltrate and what their end game would be – in other words, what loss results from the attack.
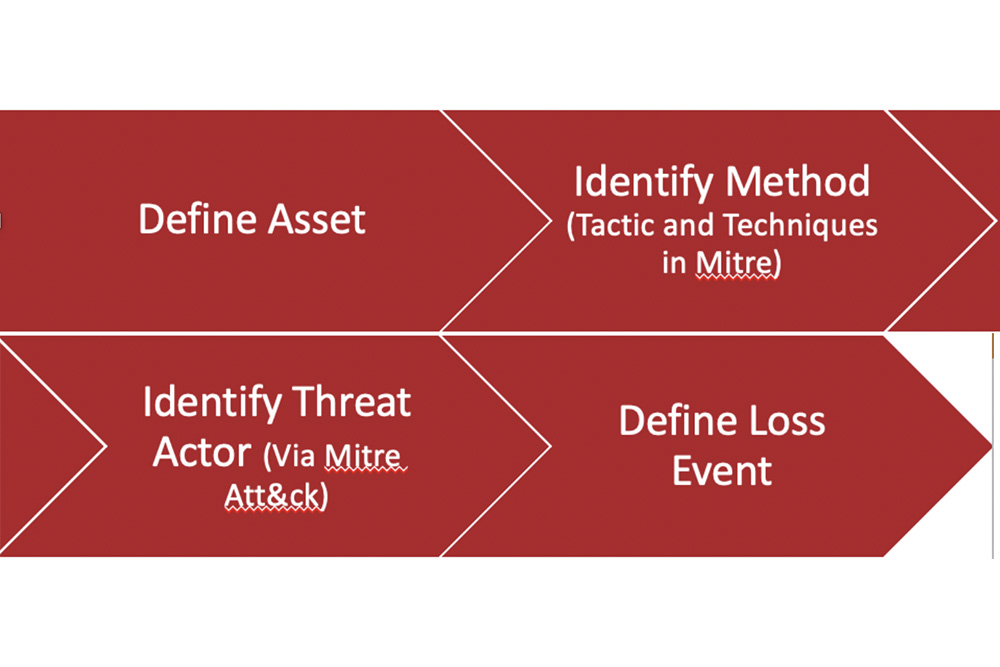
First step to identifying these key areas is to determine what assets would be targeted. Then we can look to the MITRE ATT&CK framework to identify those actors who either tend to attack certain types of organizations or have key skills in attacks against our defined assets. The scoping process with MITRE would look something like this:
It isn’t incredibly crucial to have a threat actor’s tactic or technique defined in order to scope a scenario but having those details identified helps analysts ask the right questions and have the right SMEs at the table. Using MITRE ATT&CK to scope a scenario will also help further determine the gaps in the asset’s infrastructure, allowing for a more precise remediation plan.
2. Model Loss Event Frequency with FAIR
Once we’ve scoped our scenario, we move into data gathering portion of our FAIR analysis (take a look at the FAIR model, if you’re not already familiar with it). We start with the FAIR factors Threat Event Frequency (TEF) and Vulnerability (contributing factors to Loss Event Frequency), to define how many times a threat actor would attempt to gain access to the network and how many of those attempts would result in a successful breach.
Let’s use the example of an exploit of an external facing application. First, we identified the asset, but we also identified the technique in that statement. If you look at the image below of MITRE ATT&CK matrices you can see “exploit public-facing application” listed as a technique. If we double click into that technique, it brings up threat actors that have been known to use this type of tactic, and their capabilities.
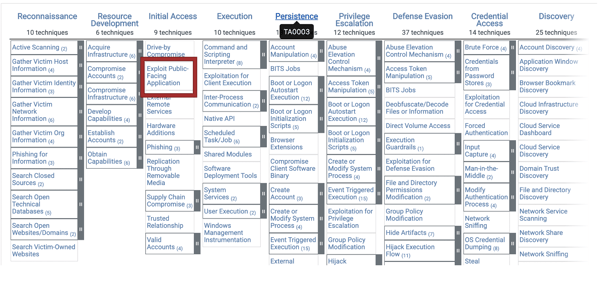
Once we’ve identified the tactic, we can identify the type of threat actor (there are a number that could target an organization by using an exploit of a public web facing application). We want to make sure we focus on those actors whose techniques are related to attacks within similar organization to ours or whose attacks are plausible based on our infrastructure.
Determining Threat Event Frequency (TEF) and Vulnerability for FAIR
Understanding threat actor tactics and techniques helps determine TEF. We can derive TEF through industry data by understanding how frequently they conduct targeted attacks. We can also derive TEF by using internal incident data, as MITRE ATT&CK helps explain how exactly our threat actor gets from point A to point B. With MITRE ATT&CK, an organization has more of a capability to look exactly where they need to within their internal data to understand if and when a targeted attack may take place.
The same level of granularity also helps to determine Vulnerability. (In FAIR, Vulnerability has a specific meaning: the probability that a threat event will become a loss event, expressed in a percentage). By understanding a threat actor’s techniques, the SMEs can help determine how the method would play out. As you look back to the MITRE ATT&CK matrices, there are two previous steps that can help identify where gaps are in the infrastructure: the reconnaissance and resource development stages. These stages tell us how attackers get into the system, how capable they are and how likely their level of capability will result in a successful exploit of a public facing application. We can also identify what controls are currently in place to prevent this type of attack and what controls may be not working as effectively as believed.
3. Understand Mitigations with MITRE ATT&CK
When looking into a specific type of attack or group, MITRE ATT&CK can help provide some controls to fix gaps. Going back to our example of an exploitation of a public facing application, in the description of this type of attack, MITRE ATT&CK provides a number of mitigation efforts. It outlines the types of efforts and how exactly that effort can prevent or protect the organization from the attack, as shown below. This gives us the ability to conduct a future state analysis with FAIR and determine the potential risk reduction with the proper mitigation plan implemented.

Why Two Models Matter
The MITRE ATT&CK Framework provides a granular level of detail that is valuable when paired with FAIR. According to FAIR creator Jack Jones, using two models in cyber risk analysis is crucial. In his blog post, Measuring Cyber Risk Requires Two Models, Not One, he explains that “any complex problem can be parsed into sub-models, which can clarify and ultimately improve measurements.” Which is one of the many reasons that pairing MITRE ATT&CK with FAIR can help organizations achieve clarity into their risk landscapes, as well as answer specific tactical questions such as “is a legacy control out of place and contributing to a severe risk?” Looking at scenarios in the most detailed view gives analysts on both the risk and cybersecurity teams the ability to identify gaps and determine what truly needs to be addressed.
Learn More:
Managing a Cyber Risk Program in an Ever-Evolving Threat Landscape









