 Here we examine three important FAIR™ terms that can confuse those learning FAIR. In addition, reference links are provided to a recently revised set of formal Open Group FAIR standards documentation.
Here we examine three important FAIR™ terms that can confuse those learning FAIR. In addition, reference links are provided to a recently revised set of formal Open Group FAIR standards documentation.
FAIR Definition: Risk
FAIR terminology certainly begins (and one could argue ends) with the term Risk. In the risk profession, it is commonly used in unclear ways – having different meanings even in a single question: ‘How much risk does that risk represent?’.
In that question, Risk in the first context is defined by the technical Open FAIR body of knowledge as the probable frequency and magnitude of future loss. In other words, Risk (from a FAIR perspective) is expressed quantitatively, in amounts of future loss and their probabilities over a given timeframe - almost always annualized.
Brad Agee is an Onboarding/Tech Support Consultant for RiskLens
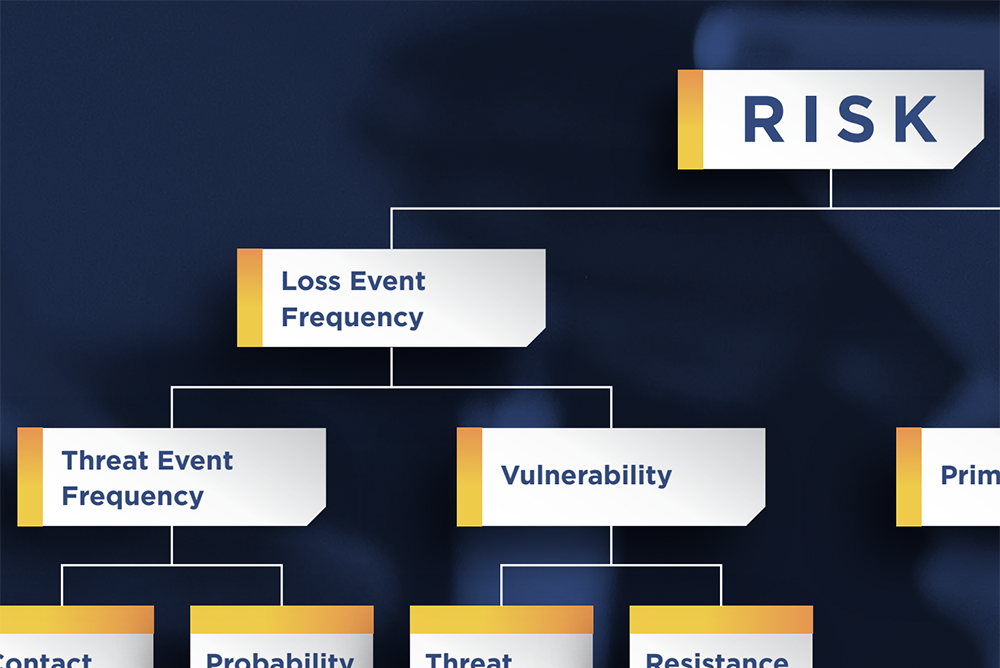
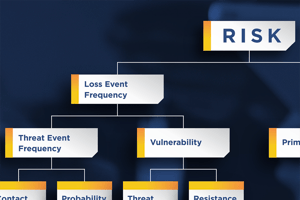
Risk in the second context is something that you can point to or refer to and say, ‘that risk’ or ‘those risks.’ The FAIR standard allows us to first, use more precise language by replacing the generic term of risk(s) with a more descriptive phrase of Loss Event(s). The FAIR standard, secondly, brings structure around a Loss Event by requiring that it be properly scoped having a Threat, Asset, and Effect.
Allow me to provide an example of scoping a Loss Event (also referred to by FAIR practitioners as a ‘Loss Scenario’) incorporating the three elements. A pre-FAIR risk professional might view “disgruntled insiders” as a risk.
A trained FAIR practitioner would visualize the three required elements to generate a Loss Scenario statement such as, “A disgruntled insider leverages weak passwords to breach sensitive consumer information residing on a network share.”
Requiring yourself and encouraging others to include the three elements in a Scenario statement helps everyone to be on the same page towards the goal of quantitatively measuring Risk.
FAIR Definition: Threat Event Frequency
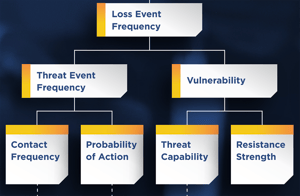 A fundamental component in any risk analysis is identifying the probability of a loss event. Unless an organization has empirical data based on actual loss experience, it is necessary to derive it from a combination of values for two FAIR standard concepts, Threat Event Frequency (TEF) and Vulnerability (Vuln).
A fundamental component in any risk analysis is identifying the probability of a loss event. Unless an organization has empirical data based on actual loss experience, it is necessary to derive it from a combination of values for two FAIR standard concepts, Threat Event Frequency (TEF) and Vulnerability (Vuln).
Threat Event Frequency is defined by the technical Open FAIR Body of Knowledge as: The probable frequency, within a given timeframe, that a threat agent will act against an asset.
Those who are just learning FAIR occasionally confuse Threat Event Frequency (TEF) with Loss Event Frequency (LEF), and this is one of the most-missed questions on the certification exam. There is a strong similarity between the definitions of TEF and LEF. The only difference is that the definition for TEF doesn’t include whether a threat agent’s actions are successful. TEF captures the number of attempts (by a threat actor) to cause harm to an Asset. A common example of a malicious threat event (where harm or abuse is intended) would be the attacker (Threat Actor) who unsuccessfully attacks a web server. Such an attack would be considered a threat event, but not a loss event.
FAIR Definition: Vulnerability
 The final term to examine is Vulnerability, the corresponding FAIR standard variable to Threat Event Frequency. Outside of FAIR, the term “vulnerability” from an InfoSec and IT perspective has a highly technical definition that permeates the industry. The FAIR standard presents a different way to consider software, hardware, or component deficiencies (Vulnerabilities) by assessing how they impact the susceptibility of the scoped asset to attempted attacks by a threat actor.
The final term to examine is Vulnerability, the corresponding FAIR standard variable to Threat Event Frequency. Outside of FAIR, the term “vulnerability” from an InfoSec and IT perspective has a highly technical definition that permeates the industry. The FAIR standard presents a different way to consider software, hardware, or component deficiencies (Vulnerabilities) by assessing how they impact the susceptibility of the scoped asset to attempted attacks by a threat actor.Vulnerability is typically estimated as a percentage for the fraction of Threat Events that become Loss Events. based on the organization’s history (gathered from SMEs) and industry resources (such as MITRE ATT&CK). In a simple formula,
Loss Event Frequency = Threat Event Frequency x Vulnerability
For more on Vulnerability, I encourage you to read this FAIR Institute blog post that provides context for how to properly think about Vulnerability both from a FAIR and cybersecurity perspective: FAIR Risk Terminology: ‘Vulnerability’ Is ‘Susceptibility’, the Open Group Says. One takeaway from this post is that from a FAIR terminology perspective, you may choose to use the term ‘Susceptibility’ in place of the term ‘Vulnerability’ and that this is formally accepted by the Open Group FAIR Standards documents.
Resources
It should be noted that The Open Group Security Forum, the experts who maintain FAIR as the international standard for cyber risk quantification, recently updated the Open FAIR Body of Knowledge to clarify some risk terminology and to simplify the Standards documents.
Open FAIR Body of Knowledge (updated Nov-’20):
Risk Analysis (O-RA) Standard, Version 2.0
The Open Group Standard (C20A, November 2020). This document provides a set of standards for various aspects of information security risk analysis. It was first published in October 2013 and has been revised because of feedback from practitioners using the standard and continued development of the Open FAIR taxonomy.
Risk Taxonomy (O-RT) Standard, Version 3.0
The Open Group Standard (C20B, November 2020). This document defines a taxonomy for the factors that drive information security risk. It was first published in January 2009 and has also been revised.
Note, reading both standards require registration (free) with the Open Group [register now].
Those desiring to learn how to apply the FAIR quantitative risk analysis model to accurately model and quantify risk and to be prepared for the Open FAIR Certification exam should consider the FAIR Analysis Fundamentals Course. The course is taught by RiskLens staff, online and live.









