FAIR Risk Terminology: ‘Vulnerability’ Is ‘Susceptibility’, the Open Group Says
 The Open Group Security Forum, the experts who maintain Factor Analysis of Information Risk (FAIR™) as the international standard for cyber risk quantification, recently updated the Open FAIR Body of Knowledge to clarify some risk terminology, including this statement:
The Open Group Security Forum, the experts who maintain Factor Analysis of Information Risk (FAIR™) as the international standard for cyber risk quantification, recently updated the Open FAIR Body of Knowledge to clarify some risk terminology, including this statement:
“’Susceptibility’ is an accepted synonym for Vulnerability.”
Read about the update from the Open Group
That makes official a working definition that many FAIR practitioners use to explain Vulnerability, an important factor in determining Loss Event Frequency in factor analysis - but one which is commonly used in a different sense in the cybersecurity world.
For the conventional definition, see this from the CVE Program, the vulnerabilities registry:
“Vulnerability: A flaw in a software, firmware, hardware, or service component resulting from a weakness that can be exploited, causing a negative impact to the confidentiality, integrity, or availability of an impacted component or components.”
So, for instance, the SolarWinds Orion software hack was carried out through a “vulnerability that could allow for authentication bypass,” said the Center for Internet Security.
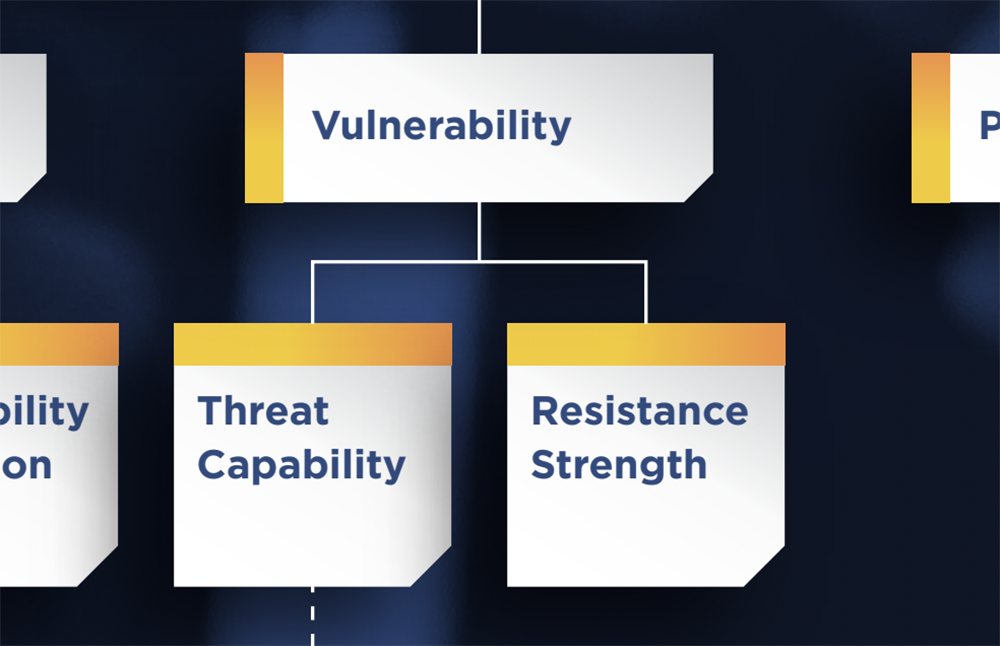
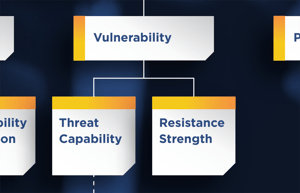
As one of the factors in FAIR that contributes to a quantitative analysis result, Vulnerability needs a definition that can be quantified. It’s a two-parter, two ways of saying the same thing, really. Take a look at the FAIR Standard on One Page infographic to see the relationship among the factors on the left or Loss Event Frequency side.
Learn FAIR from the experts - sign up for FAIR fundamentals training through the FAIR Institute
Vulnerability is the
- Probability that a Threat Event becomes a Loss Event
- Probability that Threat Capability is greater than Resistance Strength
The probability is usually expressed as a percentage, between 0 and 100%.
The Open Group unpacks the above terms:
- Threat Capability is the probable level of force (as embodied by the time, resources, and technological capability) that a Threat Agent is capable of applying against an Asset.
- Resistance Strength is the strength of a Control as compared to the Threat Capability.
Vulnerability is typically estimated as a percentage for the fraction of Threat Events that become Loss Events. based on the organization’s history (gathered from SMEs) and industry resources (such as MITRE ATT&CK).
As Steve Poppe writes in his blog post for the FAIR Institute, What Is Vulnerability?, estimating Loss Event Frequency for FAIR comes down to
Loss Event Frequency = Threat Event Frequency x Vulnerability
He gives this simple example:
Suppose the loss event is the exposure of confidential information to unauthorized users, and we need to evaluate loss event frequency for two threat types, loss of a laptop and malicious use of privileged access by an insider.
|
Scenario |
Loss of Laptop |
Malicious Insider |
|
Threat Event Frequency (annual) |
10 |
0.1 |
|
Vulnerability (probability Threat Event will result in a Loss Event) |
1% |
25% |
|
Loss Event Frequency (annual) |
1 x per year |
.025 times per year (once every 40 years) |
Now, imagine Susceptibility in place of Vulnerability above, and you’ll see why it’s a useful synonym both for understanding and communicating FAIR methodology and avoiding confusion with the “vulnerabilities” that the security world is forever hunting down.
Related:
'Vulnerability' in Risk Analysis, Explained in 2 Minutes [Video]
Threat Capability and Resistance Strength: A Weight on a Rope
Meltdown, Spectre, Heartbleed - Risk Modeling the Vulnerability du Jour, Part 1: Framing









