UNPACK: The UnitedHealth Group Hack - A Billion Dollar Cyber Loss Event Through the Lens of FAIR


In this article, I break down the UnitedHealth Group cyber-attack, giving an easy-to-understand overview packed with insightful details. I utilized the FAIR Materiality Assessment Model (FAIR-MAM) to quantify losses, drawing on data from UnitedHealth Group Incorporated's SEC Form 8-K/A (Amendment No. 2) filed on April 24, 2024, the Q1 earnings call, and Congressional testimony alongside lists of class action legal filings and regulatory investigations, and more sources.
Mohammad Arif is a FAIR practitioner and a Security Leader based in Melbourne, Australia
This analysis also incorporates contextual data from other public sources to provide a comprehensive financial impact assessment. It outlines the significant disruption caused by the "Blackcat / ALPHV" ransomware group, which began its attack on February 21, 2024, targeting UnitedHealth Group’s payments processing subsidiary Change Healthcare - a critical component of the U.S. healthcare system.
The attack led to substantial service disruptions, affecting pharmacy refills, insurance transactions and healthcare facilities. The fallout prompted UnitedHealth Group to acknowledge the attack publicly, focusing on service disruptions without detailing the extent of data compromised.
This event has heightened awareness around the vulnerability of healthcare infrastructure to cyberattacks, catalyzing calls for stronger cybersecurity measures across the sector. Federal agencies like the FBI, CISA, and the Department of Health and Human Services are actively involved in addressing the threat, underlining the need for improved security protocols to protect critical healthcare services and patient care globally.
Combining the direct response costs and the lost revenue, the total financial impact ranges from a minimum of $1.45 billion to a potential maximum of around $1.6 billion for the year (including a ransom payment of $22 million). These figures reflect significant financial strain due to both the direct costs of addressing the cyberattack and the broader operational and reputational damage impacting revenue streams.
I have divided this post into two sections: 1) a detailed, cyber-focused look at the impact of the hack with FAIR-MAM and 2) a high-level look from a financial perspective on UnitedHealth.
What is FAIR-MAM?
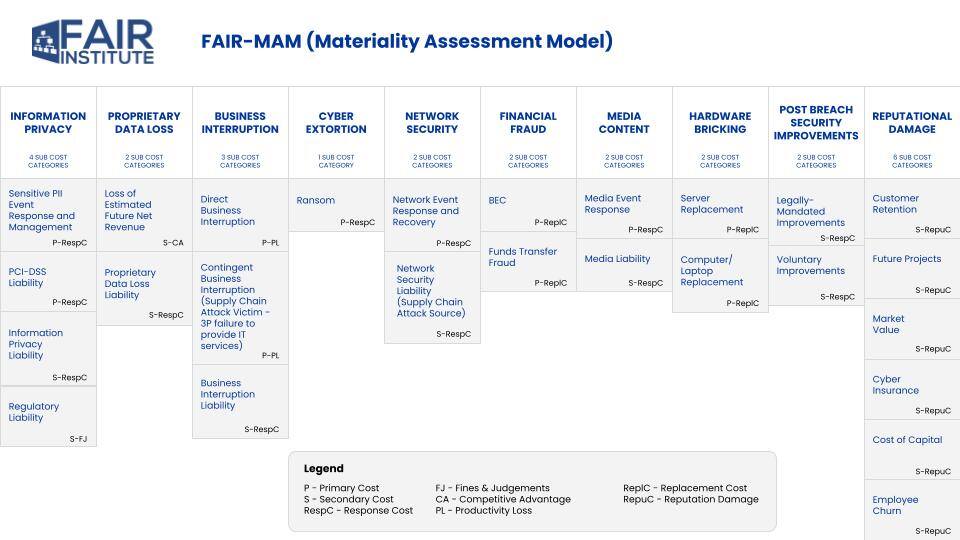
The FAIR Materiality Assessment Model is part of the family of models and standards derived from Factor Analysis of Information Risk (FAIR). FAIR-MAM gives analysts a deeper, wider look at the cost data for cyber incidents. The model offers more than 200 micro cost drivers within 10 discrete loss modules to fine tune the quantification of loss data.
See a high-level look at FAIR-MAM categories here:
See FAIR-MAM in Action: The FAIR Institute is tracking the impact of hacks in the news at How Material Is That Hack.org, a joint project with our technical advisor, Safe Security.
FAIR-MAM Analysis
Analyzing the cyberattack on Change Healthcare within the FAIR Materiality Assessment Model (FAIR-MAM) highlights extensive impacts across several (though not all) of the 10 loss categories. I also grouped the impacts as the Primary or Secondary costs (see the key at the bottom of the FAIR-MAM chart) that we know from traditional FAIR risk analysis.
Primary Loss Categories:
- Information Privacy
- Sensitive PII Event Response and Management: The exfiltration of sensitive data such as PHI, insurance, dental records, payment information, and Social Security numbers affected an estimated 152 to 210 million record holders.
- Customer Support Related Costs: Not explicitly quantified but involves undertaking breach notifications and related administrative requirements.
- Business Interruption
- Direct Business Interruption: Lost revenues amounting about $280 million for Q1:24, with projected total losses for the year between $350 million and $450 million due to service interruptions at Change Healthcare.
- Contingent Business Interruption: Not explicitly mentioned but implied through operational disruptions affecting third-party providers linked to Change Healthcare.
- Cyber Extortion
- Ransom: UnitedHealth paid a reported $22 million (350 Bitcoin) to a group identified as BlackCat / ALPHV, as part of efforts to protect patient data from further disclosure.
- Network Security
- Network Event Response and Recovery: About $595 million were spent in direct attack response costs across different UnitedHealth divisions, primarily for clearinghouse platform restoration and other immediate response efforts.
Secondary Loss Categories:
- Information Privacy
- Regulatory Liability: Change Healthcare is currently under scrutiny from several bodies. The US Department of Health and Human Services, Office of Civil Rights has initiated an investigation for HIPAA violations. The US Department of Justice reportedly will re-open an antitrust investigation of the Change Healthcare acquisition. Both houses of the US Congress held hearings. US state attorneys general have already sent a warning letter to UnitedHealth. Furthermore, there have been multiple class action legal filings.
- Proprietary Data Loss
- Proprietary Data Loss Liability: No specific information available on what was stolen in this category, but the loss of sensitive business information could lead to future legal challenges.
- Legally Mandated and Voluntary Improvements: The company will provide free credit monitoring and identity theft protection for two years and a “dedicated call center staffed by clinicians” for clients.
- Customer Retention, Future Projects, Market Value: The breach's scale and its impact on services may lead to long-term damage to UnitedHealth's and Change Healthcare's reputation, potentially affecting customer trust and market standing.
Financial Analysis
Based on the available data in public domain, here's a summary of the “Net Financial Loss” and overall impact experienced by UnitedHealth Group due to the cyberattack:
Direct Response Costs:
UnitedHealth Group reported direct attack response costs totalling about $595 million for Q1:24, with a projection for the full year to be between $1 billion and $1.15 billion. These costs stem from efforts to restore systems and manage the immediate fallout of the cyberattack, including medical expenses incurred due to halted care management activities.
Lost Revenue:
The disruption caused by the cyberattack led to significant revenue losses. For Q1:24, the revenue loss was $280 million, with the total expected loss for the financial year projected between $350 million and $450 million. This loss of revenue is a direct result of operational disruptions in Change Healthcare’s services, impacting the ability to process transactions and deliver services.
Ransom Payment:
A ransom of approximately $22 million (estimated at 350 Bitcoin) was paid to mitigate the impact of the cyberattack and prevent further data disclosure.
Share Price Impact:
>>The total quarterly impact from the cyberattack was 74 cents per share
>>Expected full-year impact ranges between $1.15 and $1.35 per share
Operational Disruption of Healthcare Providers:
The disruption affected numerous healthcare providers, impacting 6,000 hospitals, 1 million physicians, 125,000 dentists, 39,000 pharmacies, and 700 laboratories. These entities faced significant challenges in processing prescriptions and conducting authorization checks, directly harming patient care and operational efficiency.
Number of Records and Transactions Affected:
The cyberattack threatened the integrity of estimated 152 to 210 million records and disrupted an infrastructure that supports 15 billion transactions annually.
Additional Costs:
The data outlines several indirect and consequential costs incurred by UnitedHealth Group, including customer support, breach notifications, and free credit monitoring services. These expenses, coupled with share price volatility and operational disruptions, pose significant financial and operational challenges. The company quantified one aspect of these costs: CEO Andrew Witty testified to Congress that the company” has advanced more than $6.5 billion in accelerated payments and no-interest, no-fee loans to thousands of providers.”
Related FAIR Institute Blog Post: FAIR MAM Analysis: UnitedHealth Hack Disclosures May Significantly Under-report Total Impact
Join the FAIR Institute - Be a part of a global community sharing knowledge on advanced techniques in cyber risk management.