With all the news about Russian hackers targeting US utility plant networks, we're bringing back into view this blog post about cyber risk quantification for utility operators, by Industrial Control System (ICS) authority Michael Radigan of Leidos Cyber, Inc.
With all the news about Russian hackers targeting US utility plant networks, we're bringing back into view this blog post about cyber risk quantification for utility operators, by Industrial Control System (ICS) authority Michael Radigan of Leidos Cyber, Inc.
Simply put, when Industrial Control System (ICS) cyber risk is accurately modeled, measured, quantified and normalized with mechanical / industrial operational risk, it is then demystified.
Plant operations management needs to make effective comparisons between ICS cyber risk and the fifty other risk issues they have on their plate, ones with a historical impact on operations, to make well informed decisions. Metrics and financial analysis rule the day, management needs more than cyber risk heat maps and gap analysis against control frameworks to know how much they should care. ICS cyber risk needs to be normalized with operational risk for it to be better communicated, understood and managed.
By way of case study, allow me to showcase the output of a FAIR risk analysis performed at a power generation station where this exercise of normalizing ICS cyber risk was undertaken. For the “how-to” details, refer to the readily available and free resources given at the end of this post. (Scope and analysis results have been altered and do not reflect the actual plant cyber risk.)
Our team first analyzed four well understood mechanical loss scenarios, cause (failure) code categories, which resulted in a Forced Outage (unplanned plant shutdown) causing losses to the business. The risk analysis results were expressed in a common metric, “annualized loss exposure”. This metric can best be compared to an insurance policy premium. It is not to be confused with “annualized loss expectancy”.
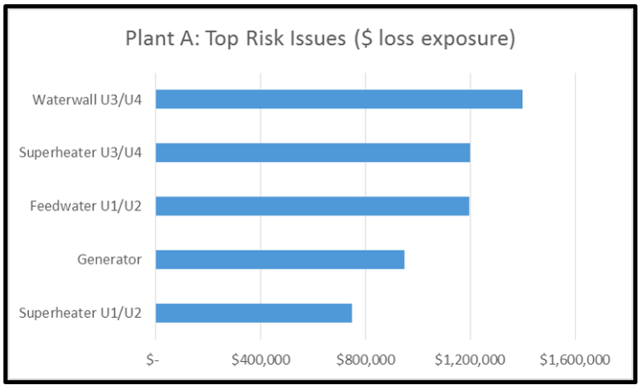
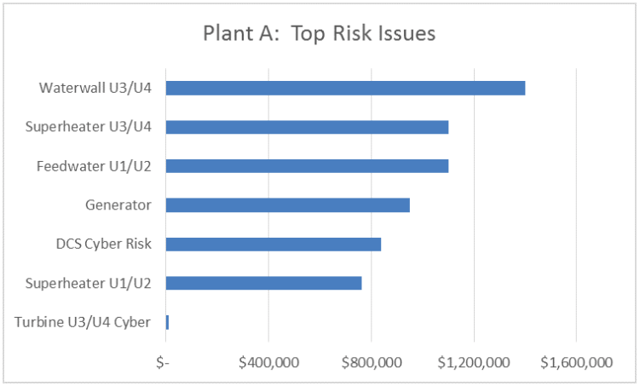
In the chart above, we see the risk (loss exposure) associated with Waterwall failures in Units 3 & 4 exceeding the risk posed by a Generator failure (Units 1-4). This stack rank did go against the intuition of the plant operations staff involved in the analysis however all agreed the results were accurate and valuable.
We then analyzed several cyber security loss scenarios of which we were most concerned with, involving two separate assets: the DCS (Distributed Control System) and Turbine Controls. We used the same proven and trusted risk analysis methodology as applied to the previously analyzed mechanical / operational risk issues.
The cyber risk results, also expressed in the common metric of Annualized Loss Exposure, were then compared with the mechanical / operational risk issues:
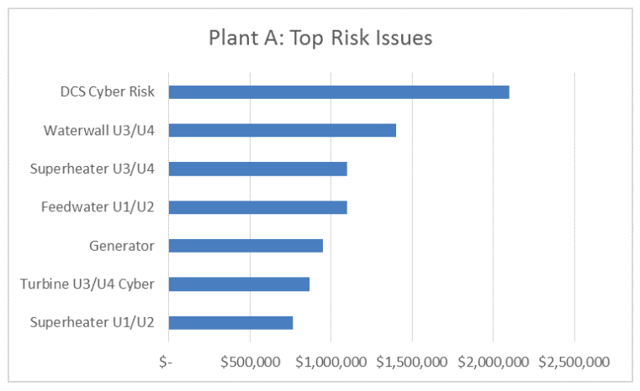
Given the current state of the DCS cyber security posture, cyber risk was at a level determined to be unacceptable. It was the desire of plant management to find mitigation options to lower DCS cyber risk to a level below Generator failure risk.
This was accomplished by performing “what-if” scenarios to compare the effect on risk of various mitigation steps. We found an optimal mitigation and risk transfer strategy that reduced the probable frequency of the cyber incident and its impact through a new file transfer policy enforced by a security appliance and a cyber insurance policy. The desired amount of risk reduction was achieved at an attractive cost/benefit ratio:
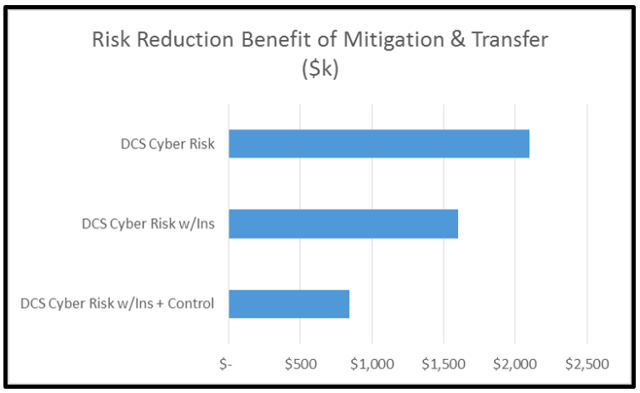
After making a well-informed risk management decision, mitigation steps taken, cyber insurance purchased, the risk issues are stacked ranked again:
ICS Cyber Risk Demystified
Cyber risk can be demystified when quantifying and normalizing it with other high-priority operational risk issues (i.e. mechanical failures, supply chain, labor, fuel costs) that are well understood. Those who are responsible for assessing and communicating cyber risk will enable the plant manager to make a rational business decision on how to manage it. The result of applying limited budget in appropriate amounts to properly prioritized risk issues results in optimal risk management and therefore more reliable and safe operations.
Suggested resources to learn more:
The foundation for measuring cyber risk in a credible fashion is to have an accurate and proven model. Such a model was published in 2008 under the Open FAIR Body of Knowledge as the Risk Taxonomy Standard by The Open Group. Using the FAIR model with a disciplined risk analysis methodology Risk Analysis Standard, scientifically proven statistical methods such as RiskLens Risk Quantification, cyber risk can be modeled, measured and quantified. I highly recommend the book entitled Measuring and Managing Information Risk: A FAIR Approach by the author of FAIR, Jack Jones.
This post originally appeared as a LinkedIn article
Also on the FAIR Institute blog:
Using FAIR to Manage Operational Risks
Announcing a new online training course -- The FAIR Analysis Fundamentals course is a foundational introduction to FAIR for analysts who want to learn to accurately model and quantify risk. Sign up for online training now!